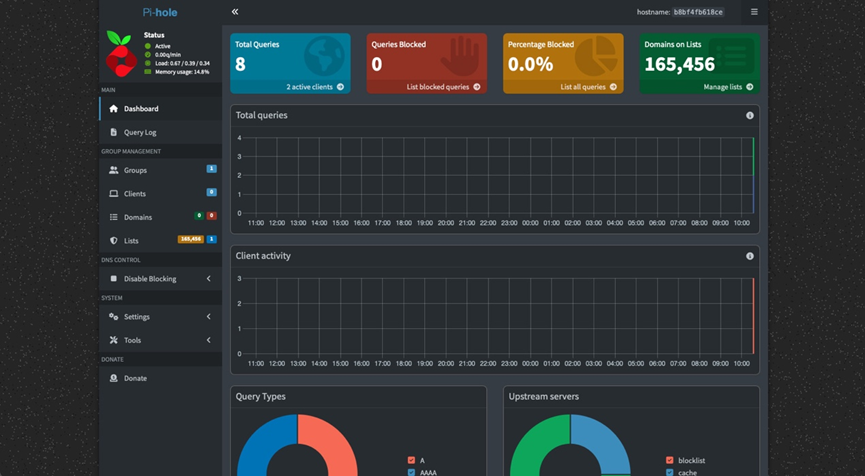
(Deploying with QNAP Container Station & Docker)
- What DNS Does: The Internet’s “Phonebook” and “Navigator”
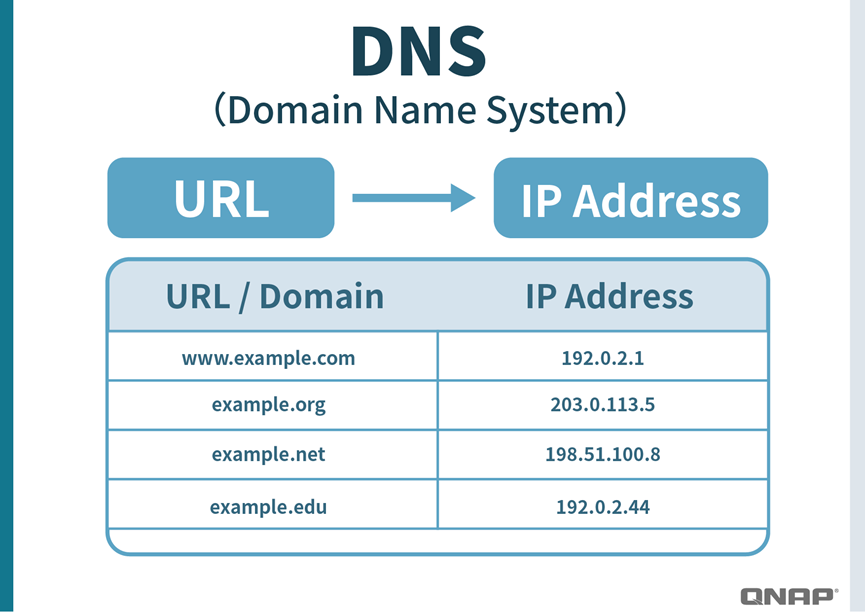
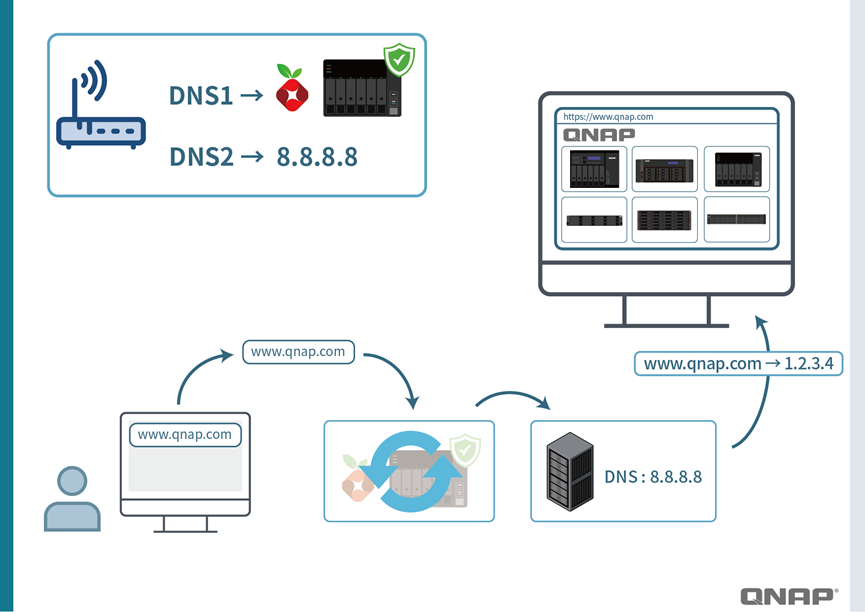
When we enter a URL in the browser, such as www.google.com, the computer actually doesn’t know its exact location. At this point, DNS (Domain Name System) acts like the Internet’s phonebook, translating the “name” into a “number,” which is the server’s IP address.
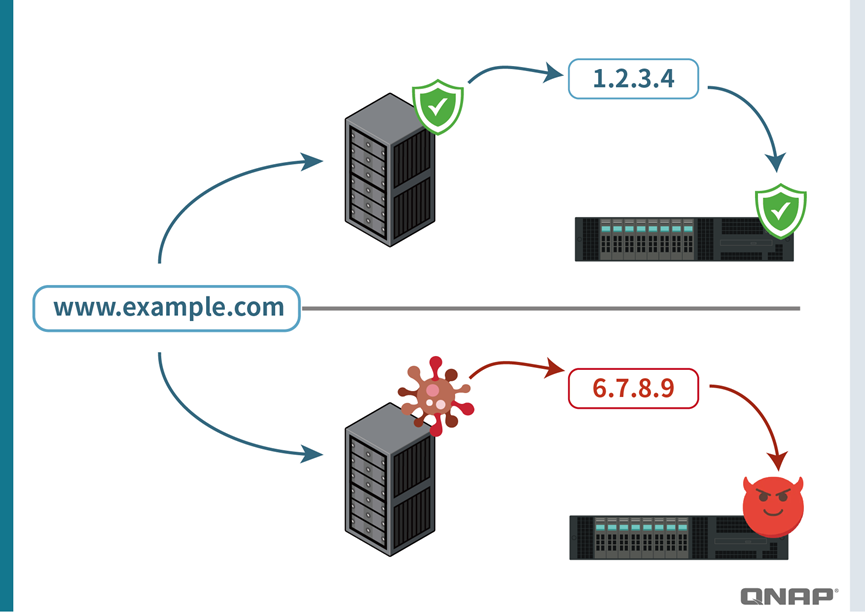
- For example: with the correct DNS, www.google.com → 1.2.3.4 (the real Google server).
- But if you encounter a malicious “fake DNS,” it may return 5.6.7.8 instead. Your computer would then be directed to a forged website that may look like Google but is actually a phishing site designed to steal your account credentials.
This also explains why DNS matters:
- Without a DNS response, a website simply won’t load. It’s like “the phonebook has been torn up and you can’t find anyone.”
- If the DNS returns the wrong IP, it misleads the user. It’s like “entering the correct address into a GPS but ending up in the middle of nowhere”.
Therefore, DNS is not just a fundamental tool for accessing the internet; it is also the first line of defense for online security.
2. How Pi-hole Works and Its Protection Principles: Your Householld’s “Network Gatekeeper”
Pi-hole acts like a “gatekeeper” at the entrance of your home network, specifically filtering out ads and suspicious websites.
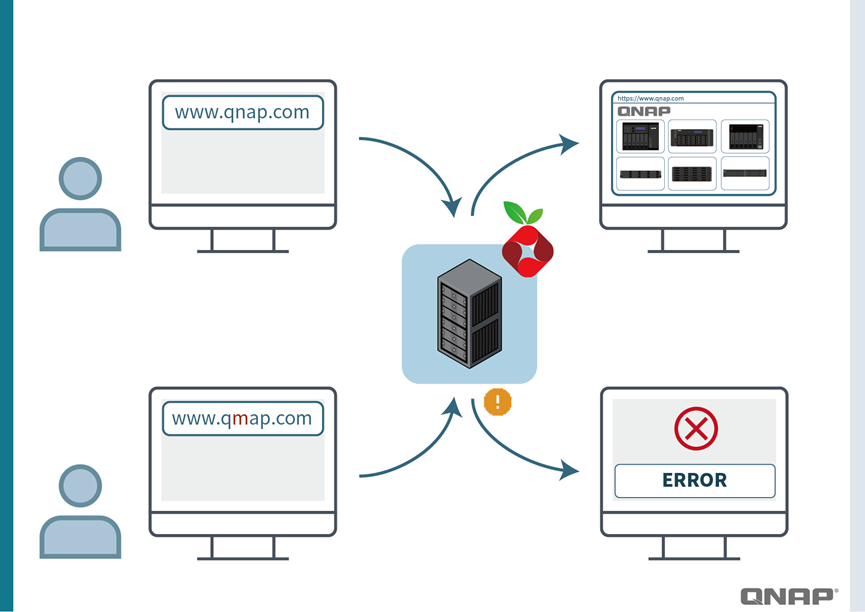
When you enter qnap.com, Pi-hole responds with the correct IP, allowing you to access the official website smoothly.
But if there’s a phishing site with a similar name (for example, qmap.com), Pi-hole checks its list, identifies it as a suspicious site, and responds with a “blackhole” (0.0.0.0).
As a result,
- your computer cannot connect to the fake website, and the browser will show an error page.
- This “preemptive blocking” method prevents accidentally clicking on malicious links, thereby protecting your accounts from compromise and your devices from malware infections.
The same mechanism can also be applied to ad blocking.
For example, a news website might send requests to ads.tracker.com to load ads. Pi-hole will “blackhole” it at the DNS level, preventing the ads from ever appearing. When you open a webpage, you’ll see only the main content instead of a screen full of ads.
Pi-hole comes with many publicly maintained blacklists (adlists) by default, and you can also manually import additional sources or even create your own whitelist (allowing specific websites to connect normally), offering great flexibility.
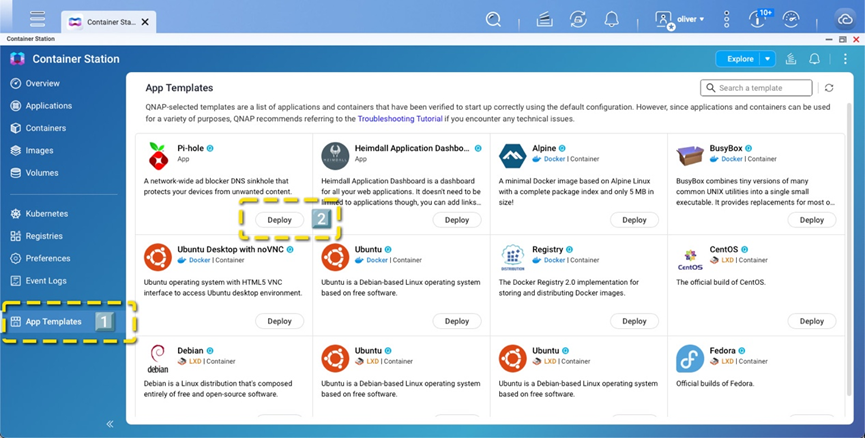
3. Setup Method: QNAP Container Station + Docker
On a QNAP NAS, deploying Pi-hole through Container Station is the easiest approach:
- Open Container Station, search for the official Pi-hole Docker image, and download it.
- When creating the container, set a static internal IP (for example, 192.168.1.10).
- Open the required ports (53/UDP, 80/TCP) to ensure DNS and the admin interface are accessible.
- After setting the admin password, you can log in to the Pi-hole Dashboard via a browser.
Since the QNAP NAS itself runs 24/7, this setup ensures Pi-hole remains continuously online, centrally managing your entire home network.
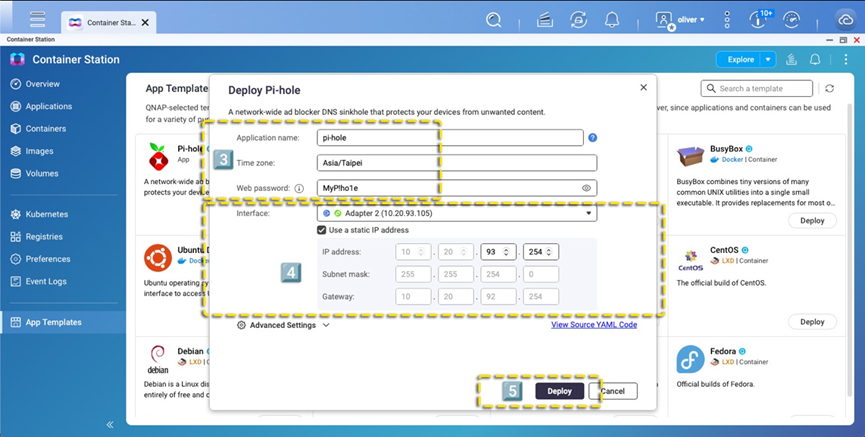
Step 3: Set up your own username and password
Step 4: Assign a static IP address to Pi-hole. This setup uses the following network configuration:
Router IP: 10.20.92.254
Subnet Mask: 255.255.254.0
NAS IP: 10.20.93.105
Assigned Pi-hole IP: 10.20.93.254
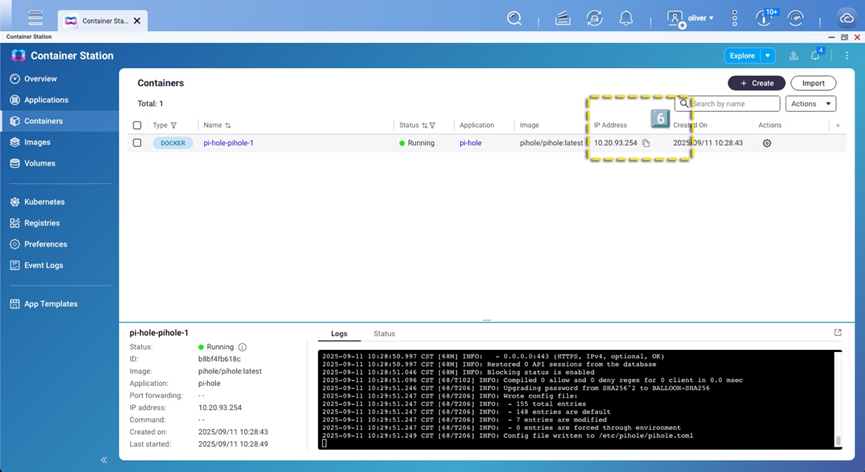
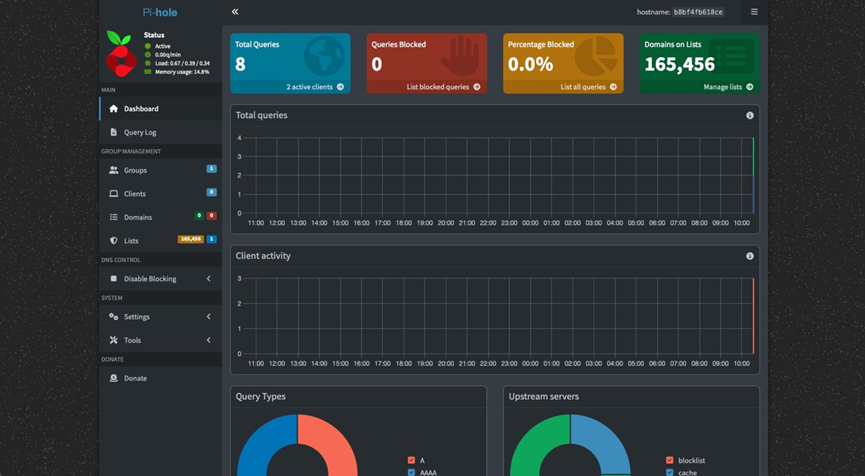
Seeing this screen indicates that the installation and setup are complete
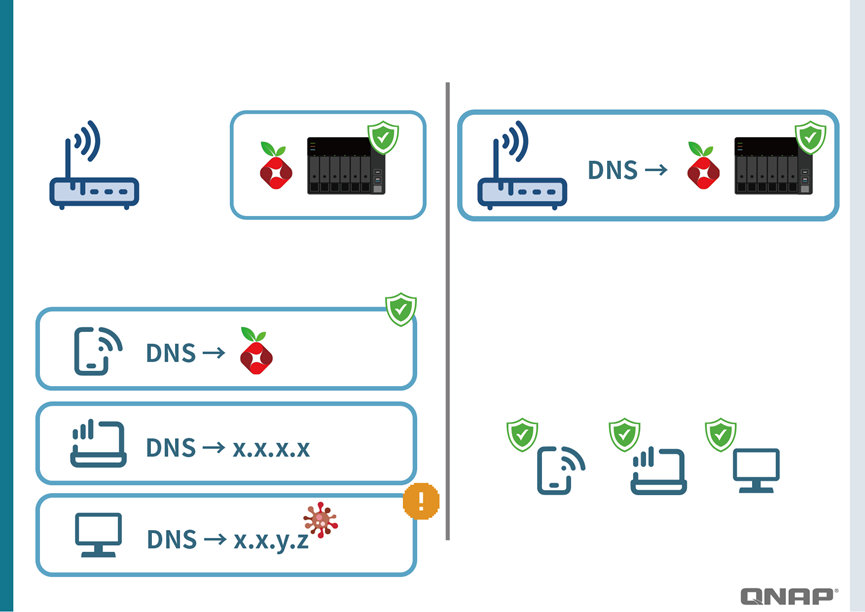
4. Home Network Configuration: Individual Setup vs. Router Setup
For Pi-hole to take effect, devices need to have their DNS Server directed to Pi-hole’s IP address.
There are two approaches:
- By Device (Individual Device Configuration)
For example, in your phone or computer’s network settings, change the DNS to 10.20.93.254 (#replace with your Pi-hole IP configured above).
Pros: Only affects specific devices, suitable for testing or single users.
Cons: Requires configuring each device individually, which is cumbersome and prone to overlook. - Router Configuration (Network-Wide)
Log in to your home router and change the DNS Server to 10.20.93.254 (#replace with the Pi-hole IP you set above).
Pros: All devices connected via Wi-Fi or wired network (computers, phones, smart TVs, IoT devices) are automatically protected.
Cons: If Pi-hole malfunctions, you need to consider backup solutions (see next section).
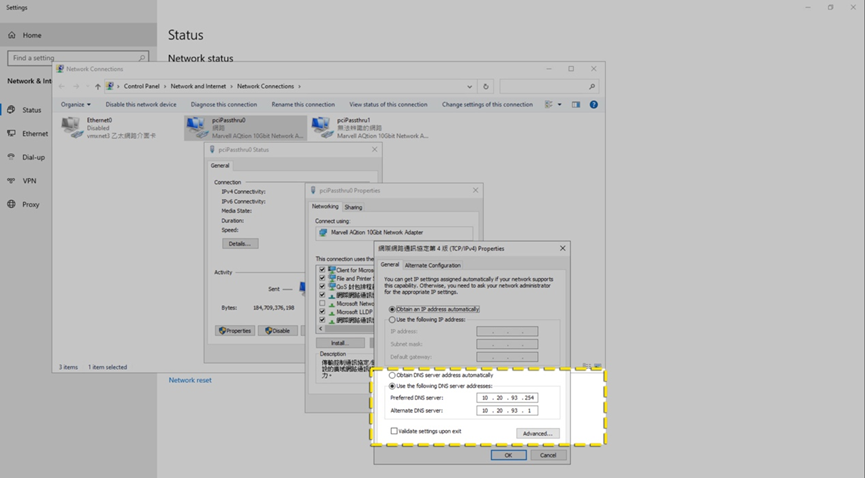
Change the DNS IP on your Windows Server system to 10.20.93.254 (#replace with the Pi-hole IP you set above).
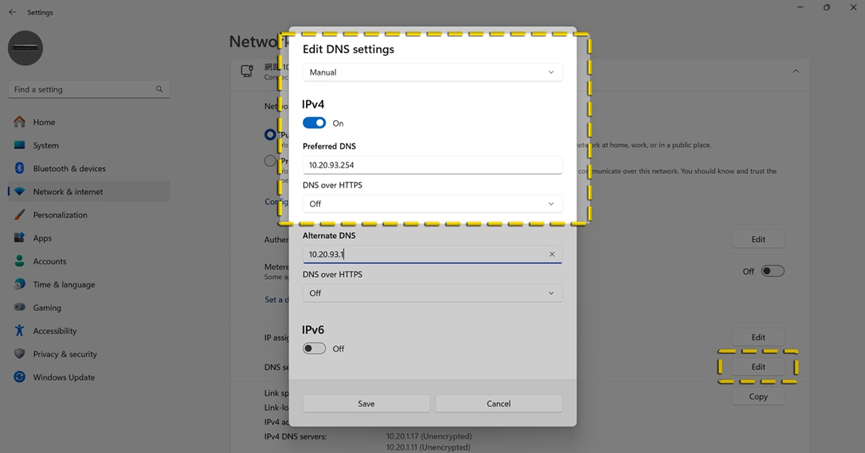
Change the DNS IP on Windows 11 to 10.20.93.254 (#replace with the Pi-hole IP you set above).

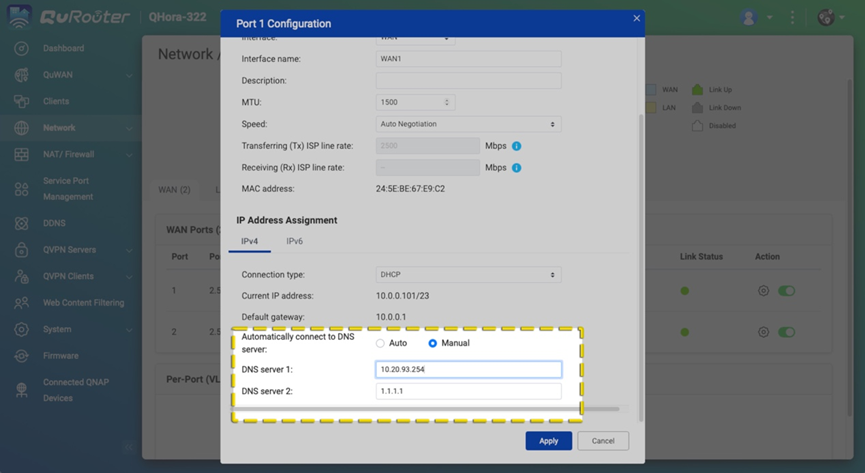
Change the DNS IP on your router to 10.20.93.254 (#replace with the Pi-hole IP you set above).
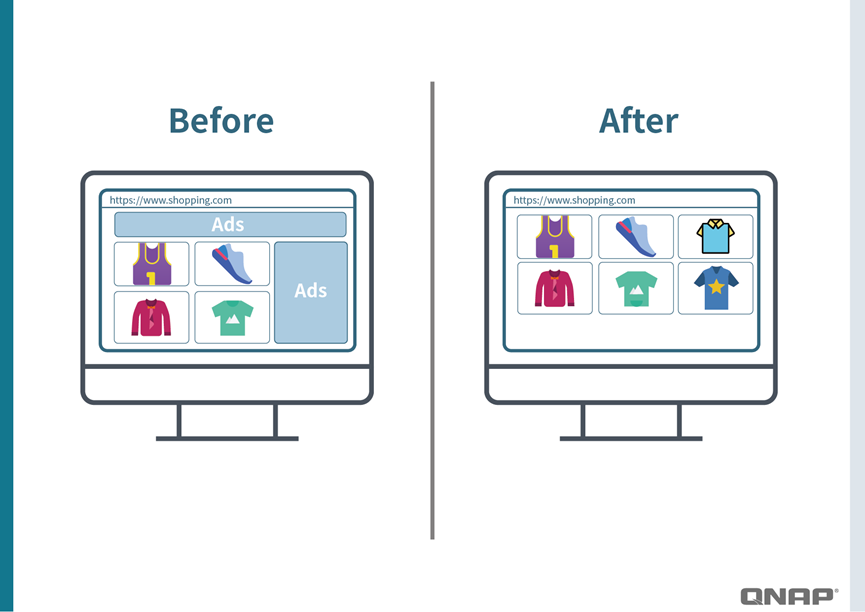
5. Before / After Comparison
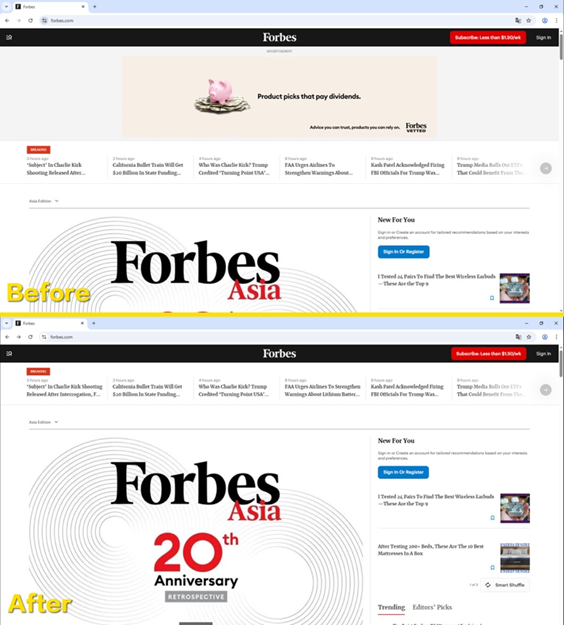
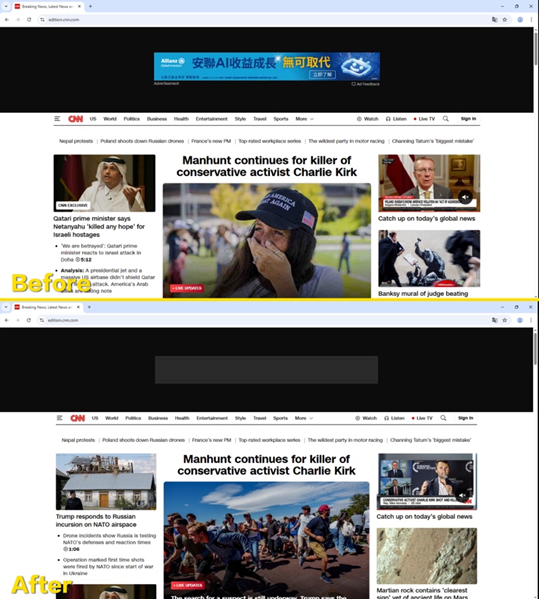
- Before: Opening a news website, you are greeted with banner ads, pop-ups, and pre-roll video ads.
- After: The same website is now clean and uncluttered, loading much faster.

6. In Case Pi-hole Fails or Goes Offline: Ads May “Temporarily Return”
Some people might worry: if Pi-hole fails, will the home networkgo completely offline?
The answer is no. Since routers or devices can be configured with a “secondary DNS” (such as Google’s 8.8.8.8, Cloudflare’s 1.1.1.1, or the DNS provided by your ISP).
- When Pi-hole is functioning normally, all queries go through Pi-hole.
- When Pi-hole encounter an issue, the system automatically switches to the secondary DNS, ensuring uninterrupted internet access.
However, note that:
- During Pi-hole downtime, ad and malicious site blocking will stop working.
- Moreover, the IPs of those ad websites may have already been resolved and cached by the secondary DNS on your computer or phone. Even after Pi-hole is restored, it may take some time (or require manually clearing the DNS cache) for the protection to return to its optimal state.
It’s like having a security guard (Pi-hole) at your home entrance on duty. If the guard takes a temporary break, a substitute (secondary DNS) from the security office steps in, but the substitute doesn’t check who the suspicious visitors are. During that period, junk ads might slip through.
7. Conclusion
Pi-hole is a powerful yet simple solution that blocks ads, malicious, and phishing websites at the DNS level, providing a cleaner and safer internet experience for the entire household.
With QNAP Container Station & Docker, you can deploy it quickly without any additional hardware.
It’s like installing an “intelligent gatekeeper” at the entrance of your home network:
- filtering out junk and malicious visitors from your network environment,
- making your devices faster and safer online,
- Even if issues occur, a secondary DNS will serve as a backup.
For anyone who values network security and a better user experience, Pi-hole is definitely worth trying.