
In the digital age, data has become the core asset of corporate operations. From customer information and financial reports to corporate decision-making data, the security and integrity of these data are crucial to a company’s survival and growth. However, with the increasing severity of cyber threats, particularly the surge in ransomware attacks, businesses are facing unprecedented challenges to data security. In such a situation, “Data Immutability” technology has gained increasing attention from enterprises. This technology provides an additional layer of protection for enterprises by preventing data modification and deletion, ensuring data integrity and protecting critical business data even in the event of a cyber attack.
In addition, data immutability is also important from a compliance perspective. Globally, more and more regulations require companies to ensure long-term storage and non-tampering of data. This is not only a safeguard for corporate information security but also an essential means of meeting regulatory requirements. This article will delve into the basic concept of data immutability, its importance for businesses, methods to prevent ransomware attacks, and how QNAP can help enterprises easily achieve data immutability through its advanced storage solutions.
What Is Data Immutability?
Simply put, data immutability means that once the data is written, it cannot be modified or deleted, and only read access is allowed. This technology is particularly suitable for long-term safeguarding of critical data. Whether it is to prevent internal errors or resist external malicious attacks, data immutability can effectively ensure data integrity. Data immutability can usually be achieved through a variety of technologies, the most common of which include WORM (Write Once, Read Many) technology and Object Lock.
Generally speaking, data immutability provides a more secure data management environment for enterprises by preventing data tampering. Particularly when coping with internal operation errors, external cyberattacks or regulatory requirements, this technology has become an effective means of safeguarding data security.
Importance of Data Immutability in Today’s Enterprise
- Protecting Sensitive Data
In modern enterprises, data is not merely a byproduct of operations, it has become a crucial component of the core business. Whether it is customer personal information, sales data, or financial records, this sensitive data has a crucial impact on the ongoing operations of a business. As the amount of data continues to increase, enterprises need more advanced methods to protect this data from tampering, accidental deletion, or malicious damage.
Once these sensitive data are compromised, companies may face multiple losses. First of all, data loss or tampering may directly affect business operations, preventing the company from delivering services or products in a timely manner, thereby damaging customer trust. Secondly, data leakage or tampering may also cause legal and regulatory issues, which further increases a company’s compliance risk. Worse yet, a company’s reputation can be severely damaged, and reputation damage is often irreversible.
- Compliance with Regulatory Requirements
In addition to protecting sensitive data, data immutability plays a crucial role in meeting compliance requirements. With the increasing stringency of regulations around the world, businesses must ensure the long-term preservation and immutability of data to comply with legal requirements. For example, the European Union’s GDPR (General Data Protection Regulation) imposes strict regulations on the processing of personal data, including transparency and security in data protection. Similarly, in the United States, HIPAA (Health Insurance Portability and Accountability Act) requires medical institutions to protect patient data and ensure its data integrity.
Data immutability technologies, such as WORM (write once, read many) and Object Lock, provide the technical foundation for enterprises to comply with these regulations, ensuring that they can operate securely and in compliance with regulatory requirements.
Lessons from History: Ransomware Attacks
In fact, many enterprises have learned the importance of data immutability from major cyberattacks in the past.
Ransomware is a type of malicious software that encrypts a company’s data and demands a ransom from the victim in exchange for a decryption key. In recent years, the number and complexity of ransomware attacks have been on the rise, and companies of all sizes have become targets for these attacks. Usually, ransomware enters the corporate network through phishing emails or system vulnerabilities, and then encrypts the company’s critical data, causing the business to fail to operate normally. If companies are unable to restore data in a timely manner, they may risk business interruption, customer loss, and damage to brand reputation.
The 2017 WannaCry ransomware attack affected hundreds of companies around the world, forcing their operations to a standstill as their data was encrypted. The hackers demanded huge ransoms from these companies in exchange for decrypting the data. However, for companies that had adopted data immutability technology, the situation was quite different. These companies could quickly resume operations from their immutable data storage without having to pay a ransom.
These real-life cases highlight the value of immutable data in defending against cyber threats. As ransomware attacks become more frequent, data immutability will be a crucial weapon for enterprises in tackling future security challenges.
How Data Immutability Helps Enterprises Prevent Ransomware Attacks
While enterprises can reduce the risk of attacks through various measures, such as strengthening network defenses and regularly backing up data, these methods are not enough to completely eliminate the threat of ransomware. Especially when an enterprise’s backup system itself is attacked, traditional backup solutions may not provide adequate protection.
Data Immutability as Protective Measure
Data immutability technology has shown tremendous potential in defending against ransomware attacks. Through technologies such as WORM or Object Lock, enterprises can ensure that data cannot be modified or deleted once written. Even if hackers successfully infiltrate a company’s system, they are unable to encrypt or alter immutable data. This means that even if an enterprise’s primary data system is attacked by ransomware, they can still quickly resume normal operations with immutable data without having to pay a ransom to the attacker.
Key Technological Elements for Data Immutability
To achieve data immutability, enterprises often rely on a combination of technologies to ensure data security. Here are some key technological elements:
1. WORM (Write Once,Read Many):WORM It is a common data immutability technology. Its core concept is to allow data to be written once, after which it can only be read and cannot be modified or deleted. This technology is widely used in industries that highly rely on data integrity, such as finance, law, and medicine. For example, financial institutions need to keep a large number of transaction records. Once these records are generated, the integrity of the data must be ensured for future audit or inspection. WORM technology ensures that these data are not compromised by accidental or malicious acts. This technology ensures that once data is written to the storage device, it cannot be modified or deleted and can only be read. This can effectively prevent ransomware from encrypting or modifying stored data.
2. Object Lock (ObjectLock):Object Lock is another technology to achieve data immutability. It allows enterprises to set a “lock” time for data as needed, during which the data cannot be modified or deleted. This flexibility makes Object Lock an ideal choice for enterprises when implementing data immutability, especially when enterprises need to adjust the protection period of data based on different business needs. For example, healthcare organizations may need to retain patient records under different regulatory requirements, and these records may need to be kept for several years or longer. Object Lock can flexibly respond to such needs. With Object Lock, enterprises can set the lock time for each data object. During this period, the data cannot be modified or deleted, ensuring the security of critical data during storage.
3. Multi-tier storage architecture:When implementing data immutability, enterprises usually adopt a multi-tier storage architecture, which means that the data will be stored in different physical or cloud locations, and each layer of storage has immutability protection to further enhance data security.
QNAP’s Data Immutability Solution
As a leading provider of storage solutions, QNAP offers comprehensive data immutability solutions, helping enterprises ensure long-term data security and integrity across both cloud and on-premises deployments.
- WORM and Object Lock Technology
QNAP’s storage solutions have built-in WORM and Object Lock technologies to easily achieve data immutability. These technologies ensure that data cannot be modified or deleted once written. Enterprises can flexibly set the lock period according to their own business needs to ensure that important data cannot be tampered with during the storage period.
- Cloud Storage
For cloud storage needs, QNAP provides myQNAPcloud Storage and myQNAPcloud Object services. myQNAPcloud Storage allows enterprises to back up critical data from their NAS to the cloud and set “Compliance Mode” through data immutability to ensure long-term data security. myQNAPcloud Object is an S3-compatible object storage service with Object Lock feature to further ensure data immutability and is especially suitable for enterprise deployments that require cloud storage.
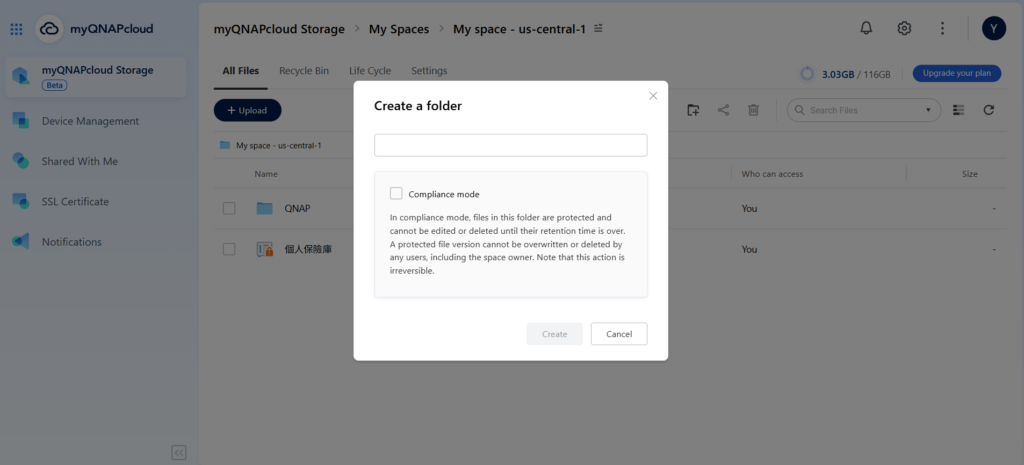
- On-Premises Storage
QNAP’s QuTS hero NAS is a high-performance storage solution based on the ZFS file system. It supports data immutability features like WORM, RAID-Z logical disk management, automatic data verification, and proactive damage prevention. Additionally, it offers data compression, deduplication, and self-healing capabilities to help enterprises efficiently manage and protect large volumes of business data. QNAP’s QuObjects is an S3-compatible object storage platform that has obtained the Veeam Ready – Immutability certification. It can seamlessly integrate with Veeam backup software to provide enterprises with a more robust data protection solution.
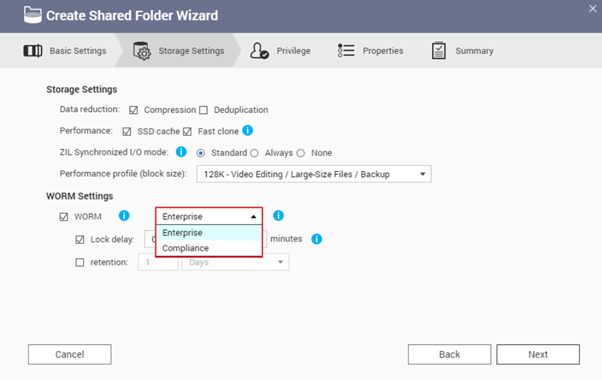
Take Action Now
Data immutability has become a necessary tool for modern enterprises to deal with data tampering threats. Whether it’s defending against ransomware attacks or meeting regulatory requirements, this technology effectively safeguards critical business data from being compromised. QNAP offers a series of advanced storage solutions, from cloud to on-premises, to help enterprises easily achieve data immutability and ensure continuous business operation.
If your company is facing data protection challenges or wants to learn more about QNAP’s data immutability solutions, you are welcome to contact the QNAP business team for more professional advice and technical support.