
When data accumulates rapidly, users often store large amounts of documents, images, videos, or emails on the NAS. However, traditional folder structures or keyword-based search methods often fail to accurately locate the needed files. To address this pain point, a search tool that can understand content and quickly locate files becomes essential, and Qsirch is the intelligent search engine built for that.

In addition to using keywords or metadata, such as file names, content, modification dates, author names, and other factors, to quickly locate relevant files and documents, an AI-powered semantic search feature has now been added. With this feature, users can simply enter a description of a photo, such as “a puppy running on the grass” and find all related images.
This year marks a milestone update that supports AI Retrieval-Augmented Generation (RAG) search technology powered by the generative capabilities of Large Language Model (LLM). It helps enterprises extract key information more accurately and efficiently from the massive datasets stored on NAS. It not only quickly identifies the most relevant content to your needs, but also accelerates decision-making, optimizes workflows, and fully unleashes the true value of data.
Today, we’ll demonstrate how to use Qsirch with ChatGPT and RAG search to transform your NAS into a knowledge advisor for Information Security Management System (ISMS).
Install Qsirch Intelligent AI Search
Go to the AppCenter, click the Tools in the QNAP Store, and find Qsirch to install it.

The Qsirch interface appears as shown below, click the RAG icon on the right side of the search bar.

Then, click Go to RAG Settings to configure it.

It supports OpenAI ChatGPT, Google Gemini, Microsoft Azure OpenAI, and other LLM models compatible with the OpenAI API, such as DeepSeek and xAI Grok. You can choose AI models freely and integrate them into the AI search function according to your needs.

Next, we will introduce how to apply for the API keys for OpenAI and Google Gemini, respectively.
Apply for the OpenAI API Key
Log in to the OpenAI Platform with your ChatGPT account, then click Start building.

OpenAI will first prompt you to create an organization. Enter your organization name, select the description that best matches your technical proficiency, and click Create organization.

When you see the team invitation screen, click I’ll invite my team later. You can always invite members later if needed.

Next, name your API key and project, then click Generate API Key.

Copy the key and store it securely. Once the window is closed, you won’t be able to view it again.
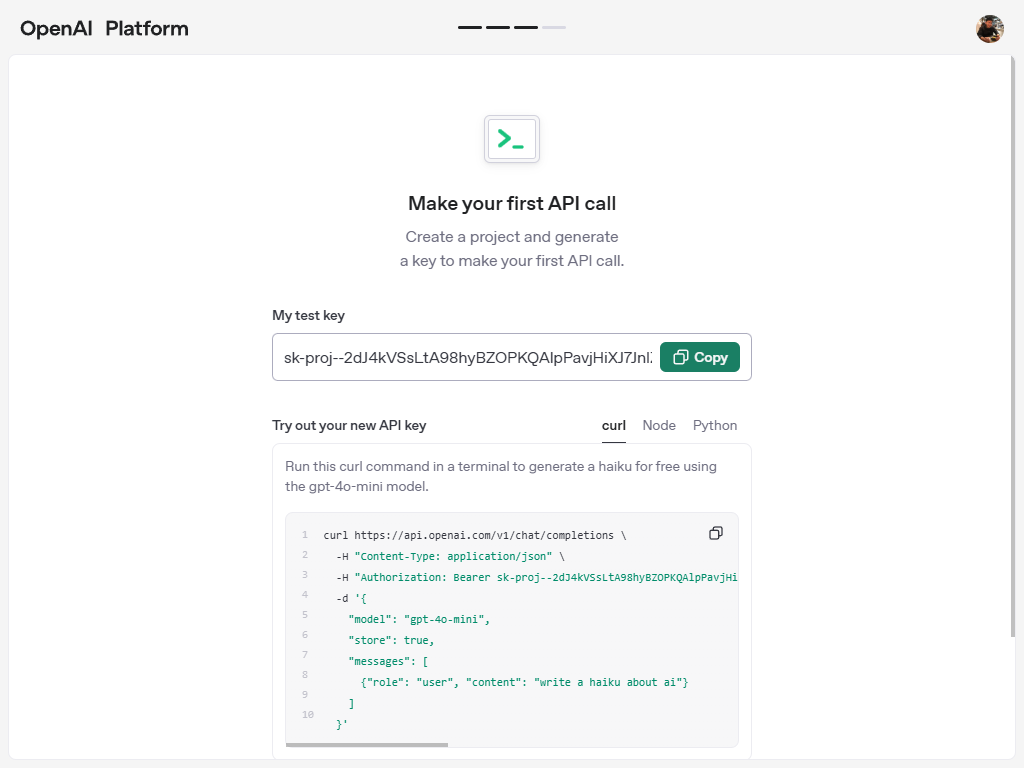
According to the Data usage for consumer services FAQ, data submitted or generated through API, ChatGPT Team, and ChatGPT Enterprise will not be used for model training by OpenAI by default.
However, you still need to add payment information to use the key normally. Click Add payment details.

Enter your credit card information and billing address, then click Continue.

Configure payment settings, including $5 minimum spend and whether to enable auto-recharge. Then, click Continue.

After verifying that all information is correct, click Confirm payment.

At this point, the API key that we’ve applied for is ready to use.
Apply for the Gemini API Key
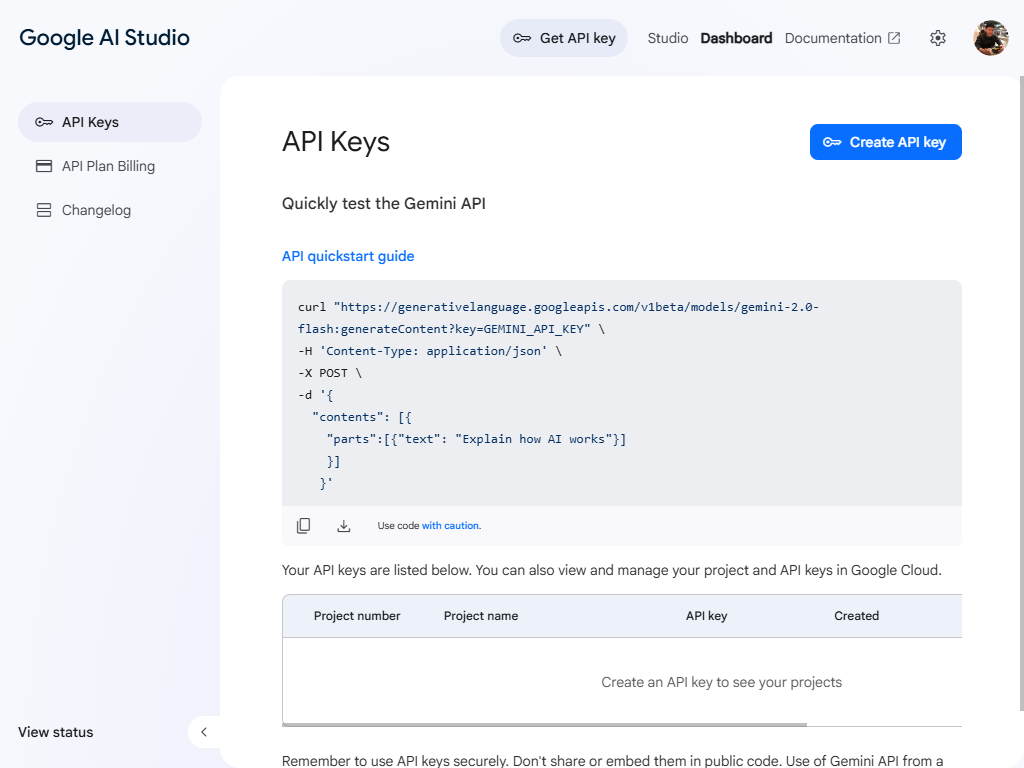
After signing in with your Google account, go to Google AI Studio, then click Get API key to apply.

Click Create API key to generate your key.
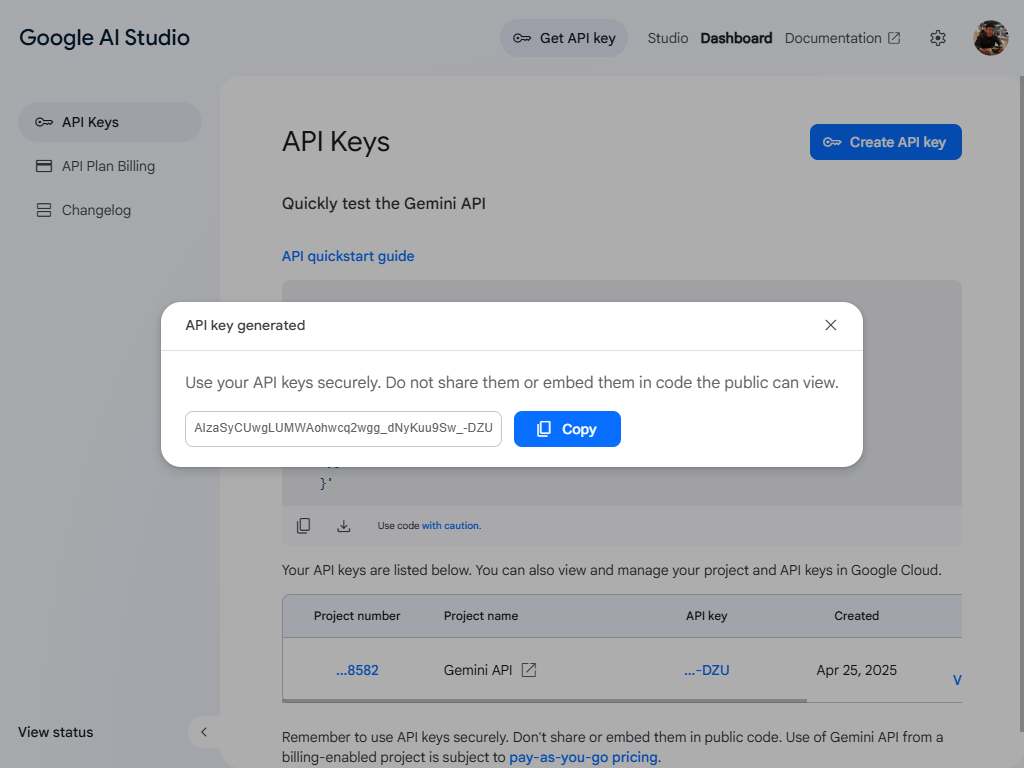
You can choose to create the API key in new project or existing project.

Copy the key and store it securely. Once the window is closed, you won’t be able to view it again.
According to the Gemini API Additional Terms of Service, when you use free services offered on Google AI Studio and Gemini API, Google will use the content you submit and any generated responses to provide, improve, and develop Google products and services, as well as machine learning technologies. Do not submit any sensitive, confidential, or personal information when using these free services.
Setting Qsirch for RAG Search
Continue to finish the LLM Settings and select OpenAI as the provider. After entering your API key, you can choose a language model.
How to choose the OpenAI Model that suits you
- GPT-4 (To be phased out soon): As the first multimodal language model capable of processing text, images, and video, GPT-4 was widely adopted across various industries. However, OpenAI has announced that support for GPT-4 will end on April 30, 2025, and it will be replaced by the GPT-4o model.
- GPT-4 Turbo: GPT-4 Turbo is an optimized version of GPT-4 that maintains powerful capabilities while focusing more on improving efficiency and reducing usage costs.
- GPT-4o: GPT-4o is currently the default model in ChatGPT, significantly outperforming GPT-4 in multiple data processing modalities such as text, voice, and image processing.
- GPT-4o mini: As a streamlined version of GPT-4o, this model is the default for users not signed in to ChatGPT, enabling them to also experience enhanced text and visual processing capabilities, along with faster response times.
We recommend using either GPT-4o or GPT-4o mini. Click Verify to confirm whether your API key is valid. If verification fails, please go back and check whether your OpenAI billing information has been properly set up.

We can customize the data retrieval scope by clicking Add.

Example scenario: Using documents related to an enterprise’s Information Security Management System (ISMS), compliant with the ISO/IEC 27001 standard, stored on the NAS. These documents cover all aspects of the ISMS:
- Information Security Policy: A formal statement of the organization’s overall information security objectives and principles.
- Procedures: Detailed descriptions outlining the steps and responsibilities for specific information security activities or processes.
- Operating Instructions: Operational guidelines and security requirements for specific equipment, systems, or tasks.
- Forms Lists: Lists of forms used to record and manage ISMS-related information.
- Records: Evidence and historical data generated from the execution of ISMS-related activities.
RAG search specifically targets the latest relevant files stored on the NAS, retrieving them in real time and uploading them to the cloud for analysis to ensure information is both timely and accurate.
Select the specific folders to include in the search and click Apply.

You can also choose the file formats to be analyzed based on your needs, including Word, Excel, PowerPoint, TXT, Email, and PDF, then click Apply.

Next, go to Qsirch and click the RAG icon beside the search bar to start using RAG search by entering a keyword.
We’ve built a dedicated ISMS knowledge base tailored for enterprises. When certification bodies conduct external audits each year, RAG search serves as our best ISMS information security management consultant.
Simulated Audit Scenario
Auditor: How does your organization ensure the effectiveness and adherence to information security policies and procedures?
- The auditor will examine whether you have set well-defined and actionable information security policies and procedures, and whether they are effectively implemented.
- They may ask how you communicate or promote these policies and procedures, how compliance is monitored among employees, and how violations are handled when they occur.
What may seem like a casual question can actually be mentally overwhelming. Even if answered directly by the CISO, delivering a well-articulated and convincing response can be quite a challenge.
Don’t rush, don’t panic, don’t be afraid. Take a look at how RAG Search can come to the rescue.
It also identifies the most relevant documents to assist in data verification and consolidation effectively.
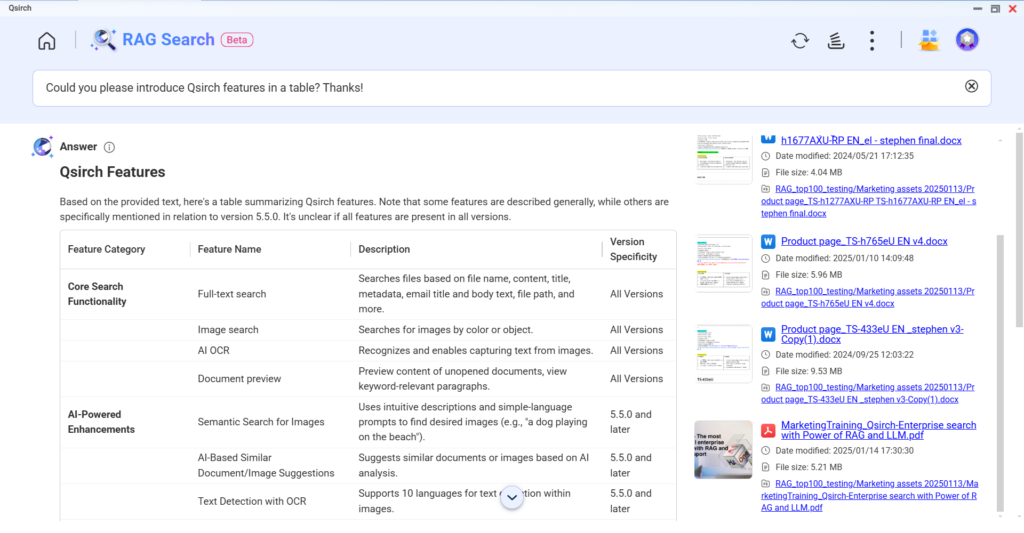
In just a few seconds, RAG Search helps us approach the issue from perspectives such as internal audits and corrective actions, management review, training and awareness, information security risk management, and resource allocation to ensure the effectiveness and compliance of our information security policies and procedures.
This allows us to respond to audit inquiries in a professional and evidence-based manner, reducing the risk of inconsistencies between verbal explanations, written documentation, and actual operations due to nervousness.
Elegant, truly elegant.
While large language models are powerful, they still suffer from some fatal flaws in real-world applications.
- Limitations and obsolescence of knowledge: The model has no awareness of new information or events that occurred after its training cutoff date, which can result in outdated or inaccurate responses.
- Generation of False Information (Hallucination): Even when it lacks sufficient knowledge in a particular field, the model may confidently generate fabricated answers, making it difficult for users to distinguish between true and false information.
- Inability to Access and Utilize External Knowledge: The model relies on its internal, parameterized knowledge to generate responses and cannot directly access or leverage external data sources. This limits its applicability in domain-specific scenarios or when working with private data.
The emergence of RAG technology has provided a highly valuable solution to these problems.
Before generating a response, RAG first retrieves relevant information from an external knowledge base and incorporates the retrieved content into the model’s input prompt. Through this approach, the model is able to generate responses based on the up-to-date data and domain-specific knowledge, which not only improves accuracy but also effectively reduces the risk of hallucination.
Embrace Qsirch RAG Search
Storing your data on a NAS for RAG search offers many advantages. Since all data resides on your own hardware, you maintain full control over access and protection mechanisms. Compared to storing sensitive information on third-party cloud servers, NAS provides more direct and customizable security measures, such as strict access control, network isolation, and even physical protection.
By implementing data encryption, regular backups, and disaster recovery tailored to your needs, the risk of data breaches or loss can be significantly reduced, ensuring that confidential enterprise information is securely and reliably used in RAG applications.
That’s all for today’s sharing. Thank you for tuning in.