Ransomware is a cryptovirology attack carried out using covertly installed malware that encrypts the victim’s files and then requests a ransom payment in return for the decryption key that is needed to recover the encrypted files. Wide-ranging attacks involving encryption-based ransomware (also known as locker) began to increase through Trojans in the past few years. This also becomes a rising threat against both business and home users that targets computers and network-based devices.
Locker is a file-encrypting ransomware (CryptoLocker, CTB Locker, TeslaCrypt, and others) that encrypts files found on local drives, removable drives, mapped network drives, and even Dropbox mappings. Victims will be extorted a ransom to decrypt the affected files, or they will be unable to open the affect files ever again. A simple yet effective method of mitigating the threat of ransomware is to ensure that you always have backups with versioning. Therefore, I will show you how to protect your data on your QNAP NAS from ransomware by using QNAP’s snapshot feature.
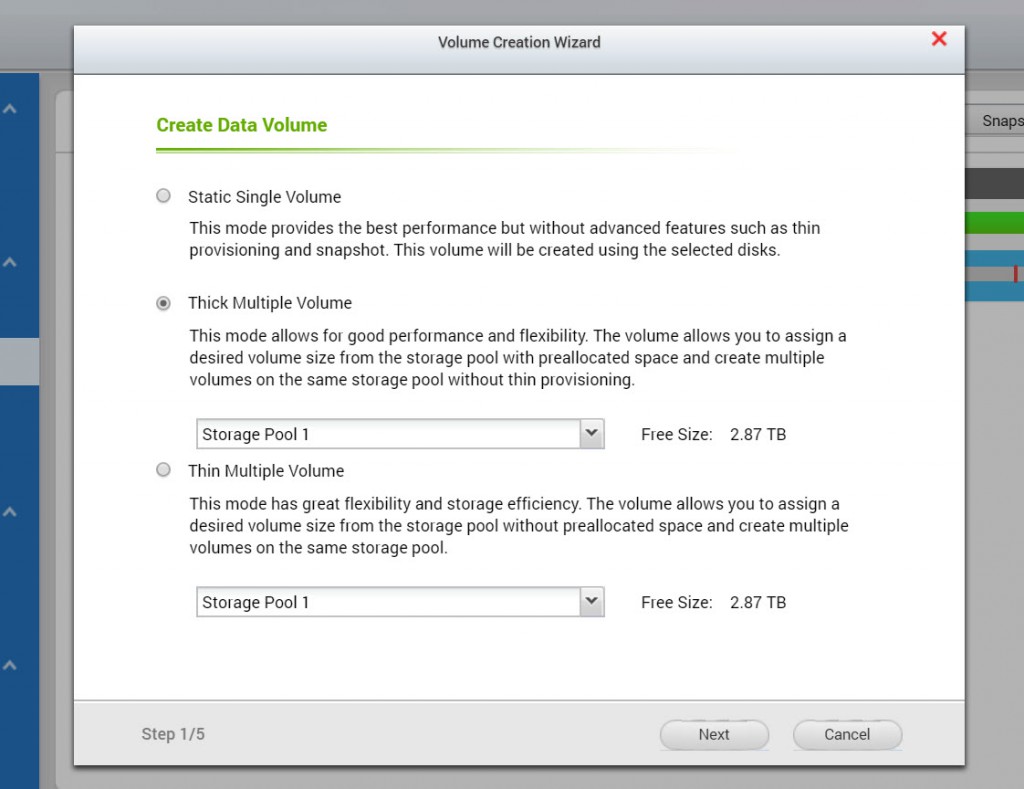
First of all, while creating your storage volume, be sure to choose either “Thick Multiple Volume” or “Thin Multiple Volume” that both support snapshot.
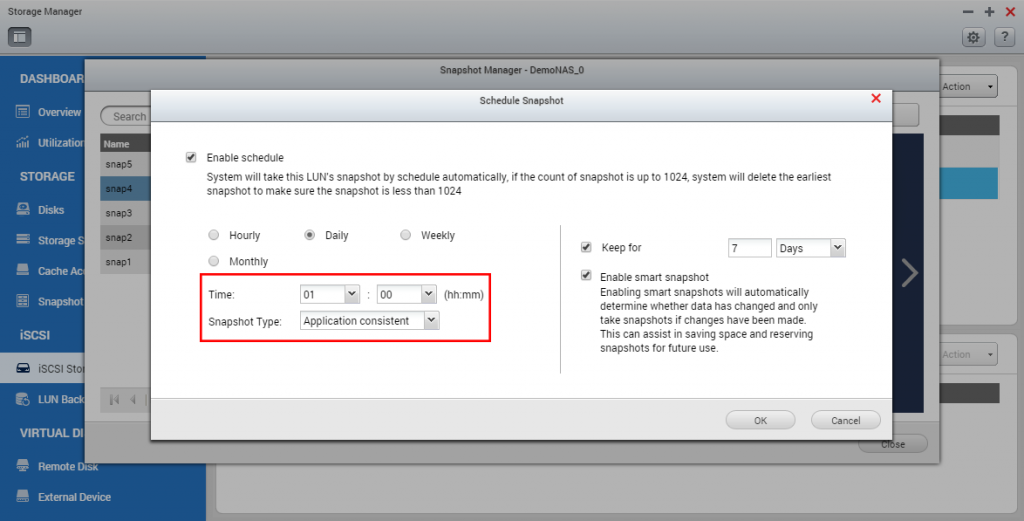
Upon finishing, refer to this tutorial and create a weekly, daily or even hourly snapshot schedule for your NAS.
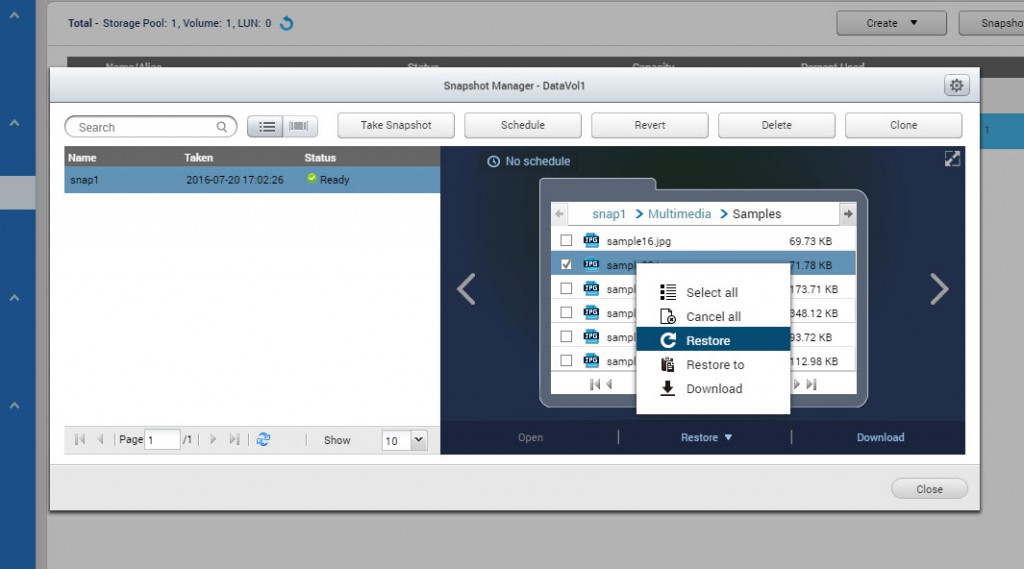
In the event of a ransomware attack and your files are encrypted by ransomware, then you can easily revert the entire storage volume to a previous state which has not been effected by ransomware. Or you can also choose to restore any specific file to a previous version and overwrite the encrypted file.
In conclusion, to avoid or minimize the damage from ransomware, it is always important to keep you NAS system up-to-date. In addition, to deploy and maintain a comprehensive backup solution with versioning, and also has the ability to quickly revert to a previous version is as important.
If someone is using QSYNC with versioning and files at the pc and ransomeware is encrypting your files, wouldn’t it be possible to revert all the changes by getting a previous version back from the NAS?
Not only ransomeware but also mining hacks are threaten to NAS. Remember to patch with the latest security on QNAP’s Security Bulletins and Advisories. An mining issue on QTS and solutions: https://amigotechnotes.wordpress.com/2017/05/03/check-and-solve-if-your-qnap-nas-has-been-injected-a-cpuminer-program/
I have unpack QNAP’s Malware Remover. 2.1.x are shell scripts to kill malware process, malware files, and add a regular check automatically. If you are interested in the detail, take a look at this post: https://amigotechnotes.wordpress.com/2017/05/04/detail-explain-of-qnap-malware-remover-2-1-0/
Hallo james.
How can you guarantee – technically – that the snapshots are not encrypted?
made this comment just to receive notifications (forgot to set it the first time).
you miss very important information that snasphots are NOT supported for ARM based models, very bad qnap!!
Hi, Bart,
The newer generation ARM is supported in the latest QNAP firmware 4.3.4. You may check it out!