
With the wave of industrial automation and smart manufacturing, the demands for cybersecurity in OT (Operational Technology) environments are increasing day by day. In the past, OT domain networking was relatively isolated from IT domain networking, leading to a primary focus on functionality and stability during the deployment, adoption, and design phases of OT systems, with less consideration for security threats. In many environments, security threats were not even quantifiable. However, as network data exchanges become more complex and frequent, various OT devices in OT environments are increasingly connected to a broader networking. With the adoption of IoT devices, smart manufacturing monitoring, and analytics systems, the lack of proper security mechanisms in OT environments can expose legacy OT equipments, production line servers, industrial computers, and machinery to cyber threats. These vulnerabilities may turn them into targets for malicious attacks or entry points for security breaches, potentially spreading infecting to other machines within OT environments, leading to business interruptions and financial losses.
This article takes the QNAP QGD-1602P Security Networking Switch as an example to illustrate how to establish an independent and secure foundational security protection environment in OT domains, physically isolating industrial computer environments, production line networks, and other networking. The deployment approach is designed for easy maintenance by IT and security personnel.
From a cybersecurity perspective, OT domains present the following characteristics and challenges:
- High Availability Requirements: Equipment and systems must operate continuously 24/7, requiring protection against disruptions caused by cyberattacks that could lead to significant losses.
- Proprietary Protocols and Systems: Many industrial communication protocols (such as Modbus, PROFINET, etc.) and industrial control systems lack mature cybersecurity protection measures.
- Lack of Real-Time Monitoring and Alert Mechanisms: Many factory networking management systems still operate within traditional frameworks, lacking real-time monitoring and alert mechanisms to detect abnormal behaviors or malware threats.
Therefore, introducing switches with malware program detection and device behavior monitoring capabilities at the OT network layer can significantly enhance OT protection capabilities. This enables real-time interception of malicious activities, allowing threats to be automatically isolated to specific network ports or designated zones, VLANs, ensuring the stability and security of various systems within the OT environment.
We actually deployed the QNAP QGD-1602P Security Networking Switch in an OT environment and connected it to other 2.5G and 1G network switches to analyze the operational status of devices within the environment.
Before powering on the device for system configuration and installation, hard drives and SSDs must first be installed in this device. It functions as both a NAS and a security network switch. One key advantage is that all security-related software and log files can be stored directly in the NAS section of this device for log aggregation. These logs can then be forwarded to other security log collection devices (such as LogMaster or other devices, QNAP NAS with WORM area, etc.) and SIEM (Security Information and Event Management) platforms like Wazuh.
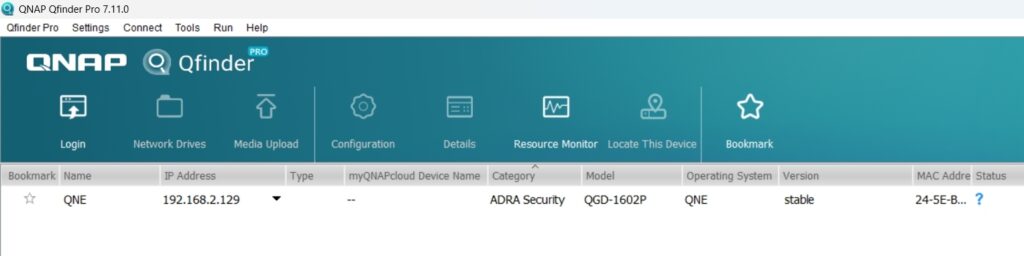
During the initial installation, you will find that the device can be detected by using QNAP Qfinder software, allowing you to locate it on the network. It is categorized as an ADRA Security product line and comes with built-in ADRA cybersecurity features.
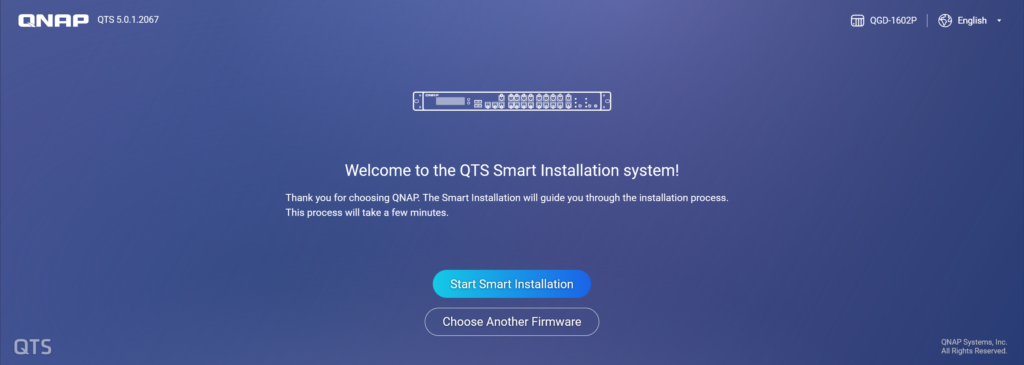
When accessing the system installation page, you will be given the option to proceed with Smart Installation or select other firmware versions to install. This is because this device can be operated with either ADRA security-enabled firmware or the standard QNAP QTS operating system.
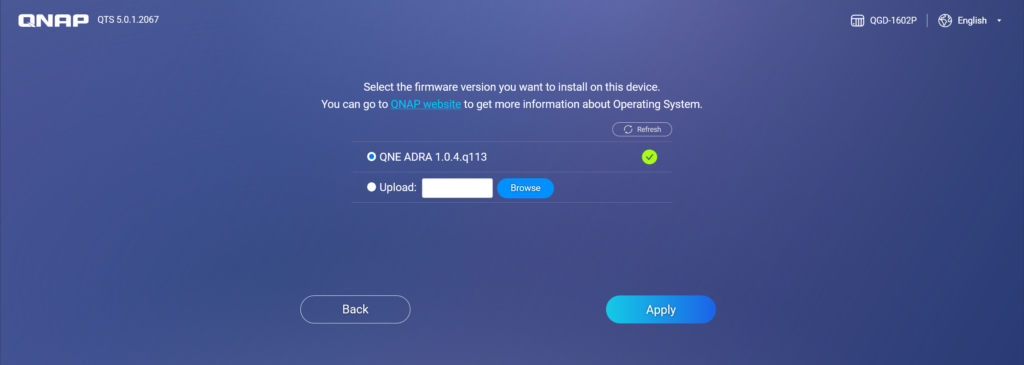
Using the current version as an example, the QNE ADRA version can be installed by default, and you can also manually upload different firmware versions to this system.
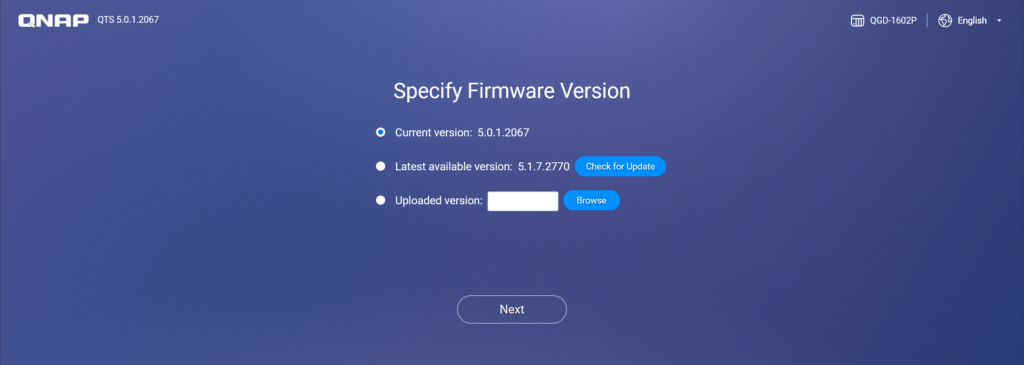
If using the QTS system, you can also select the version to install.
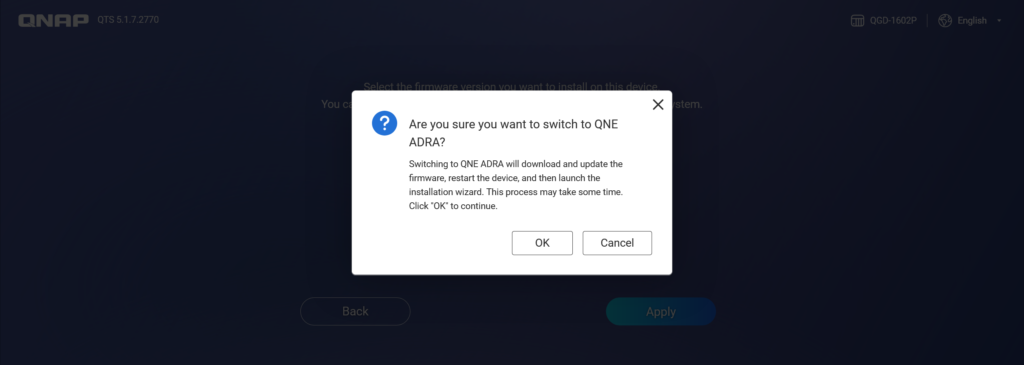
This is the screen for switching to QNE ADRA. After selecting OK, the installation process will be confirmed and proceed.
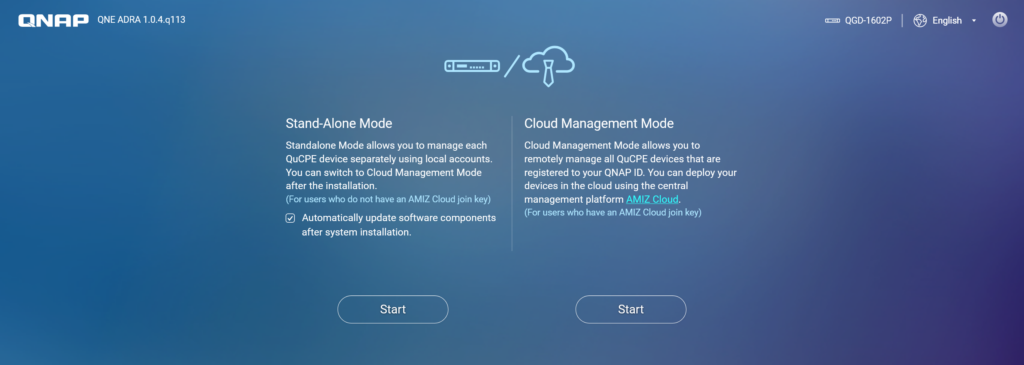
This device allows operation in either Standalone Mode or Cloud Management Mode. In an OT environment, even when using Standalone Mode, the device can still connect to the internet, enabling updates and alert functions to operate properly. However, if your OT environment policy restricts external internet access or only allows internet connectivity for updates through a firewall on a case-by-case basis, it is generally recommended to select Standalone Mode for operation. As for Cloud Management Mode, it allows personnel to conveniently manage the device via the cloud. This mode requires a QNAP AMIZ Cloud Join Key for authentication and incorporates robust security mechanisms to ensure secure remote management.
After setting up the account and password, you can proceed with the installation and configuration for use.
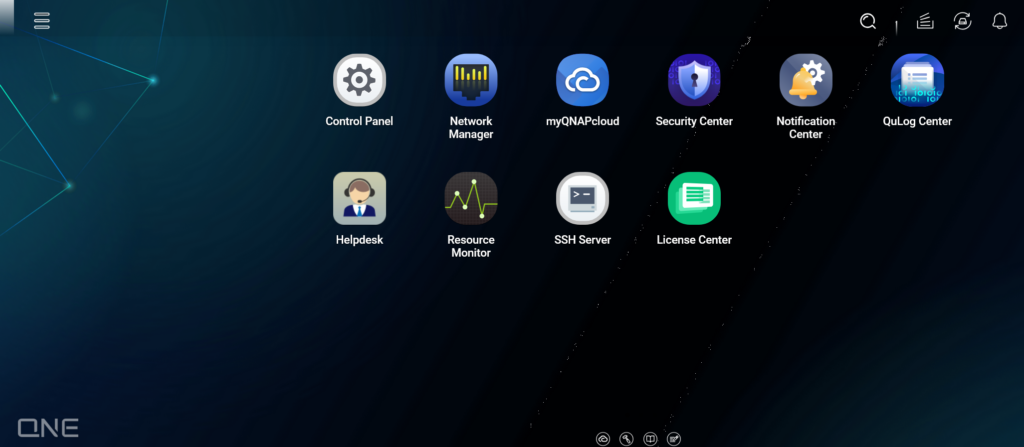
Default management interface of QGD device.
Click myQNAPcloud to see the cloud connection mechanism status of the device. If you prefer not to use Cloud Management Mode, you can switch it back to Standalone Mode for independent operation.
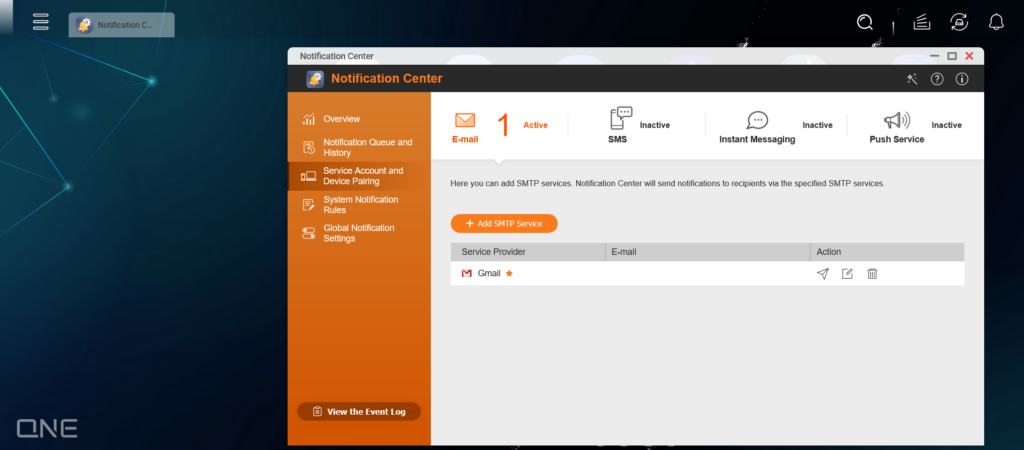
When configuring this type of device, the most critical aspect in OT environment is the cybersecurity alert function. You can choose to receive security alert notifications via email, SMS, instant messaging (IM), or webpage push services, ensuring timely awareness of potential threats.
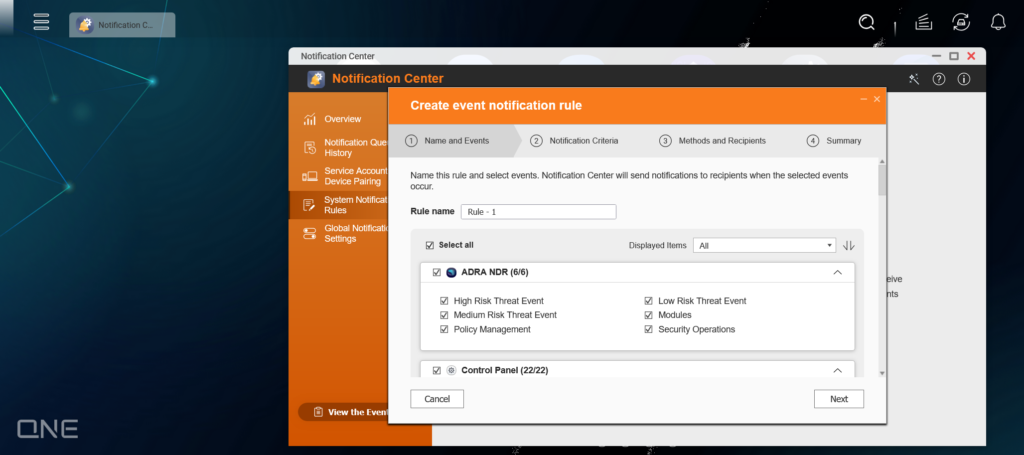
After selecting the notification method, you can configure notification rules. It is recommended to enable alerts for high-risk threats events, while medium-risk, low-risk events and other information can be configured to notify based on specific needs and circumstances.
Once the alert rules and recipient email addresses are configured, the notification setup is complete.
Switch features with malware program detection and behavior monitoring functions
1. Deep Packet Inspection (DPI)
Traditional switches primarily handle Layer 2 (L2) or Layer 3 (L3) networking exchanging, unable to perform deep analysis on industrial protocols or application-layer. However, switches equipped with malware program detection capabilities typically come with a built-in DPI (Deep Packet Inspection) engine, allowing them to identify and compare network traffic against known malware signatures. QNAP’s solution integrates ADRA NDR (Network Detection and Response) security features, which periodically updates its threat database to perform the following tasks:
- Analyze file signatures (malware signatures).
- Check whether protocol packets contain known vulnerabilities or attack behaviors.
DPI can detect industrial-specific protocols, triggering alerts or performing advanced inspection when suspicious packets or abnormal data transfers are discovered, preventing malicious files from spreading laterally within the OT area.
2. Behavior monitoring and device identification
In addition to malware detection, the switch can also perform behavior monitoring, such as:
- Device status monitoring: Detects abnormal networking behavior, such as sudden traffic spikes or drops, abnormal packet types, and promptly reports anomalies.
- Abnormal login and user permission monitoring: Monitors for continuous failed login attempts, abnormal source IPs/user accounts, and triggers alerts or access blocks.
3. Real-Time alerts and visualization
Industrial network administrators often need real-time production environment status. Therefore, switches with real-time alerting and data visualization capabilities are essential:
- Real-time event notification: When malware files or abnormal login attempts are detected, immediate alerts are sent via email, SMS, instant messaging (IM), or web push notifications, allowing administrators to take responsive action without delay.
- Visualized dashboard: Displays the connection status between devices, traffic trends, and alert events in a graphical format, making it easier for administrators to quickly identify suspicious areas.
4. Flexible deployment and integration
OT environments typically have complex structure and high system downtime costs. Switches with malware detection and behavior monitoring capabilities can significantly reduce the deployment barrier if integrated or deployed in the following ways:
- Integration with existing systems: Compatible with mainstream industrial communication protocols and legacy equipment, minimizing the need for updates to existing networking structure or equipment.
- Gradual deployment: Initially implemented at critical points (e.g., in front of high-security devices), and then gradually expanded to the entire factory.
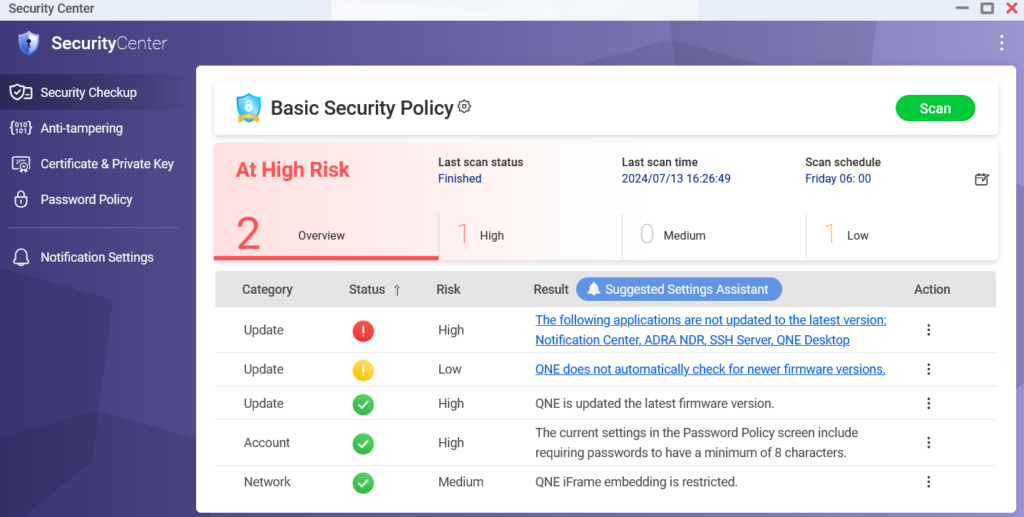
Upon accessing the Security Center in the QGD system interface, you can view the current security risk status of the device itself. This assessment applies only to the QGD device, not to the monitored devices within OT environments. Therefore, it is recommended to reduce the device’s security risks to the minimum level suggested by the system.
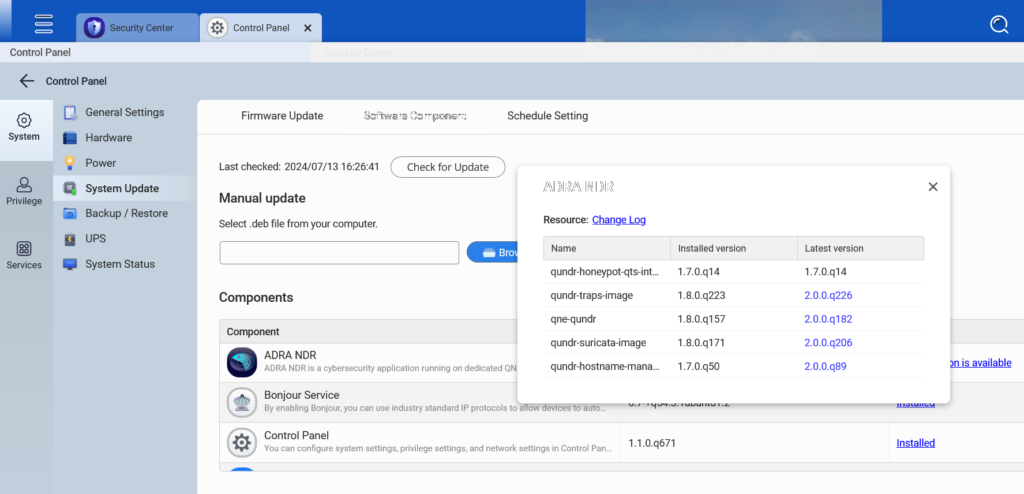
From the Control Panel of QGD, you can prioritize updating all ADRA NDR networking endpoint security protection features to the latest version.
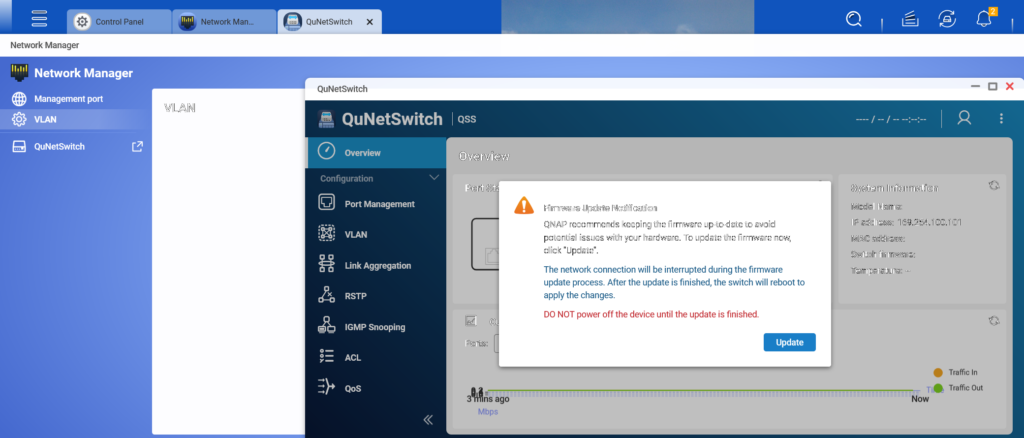
The most critical component of this product series, the QNE security network switch, must be managed through the Network Manager. It is important to note that this device functions as both a NAS and a network switch. Therefore, the network switch has its own operating system firmware, which also needs to be updated regularly.
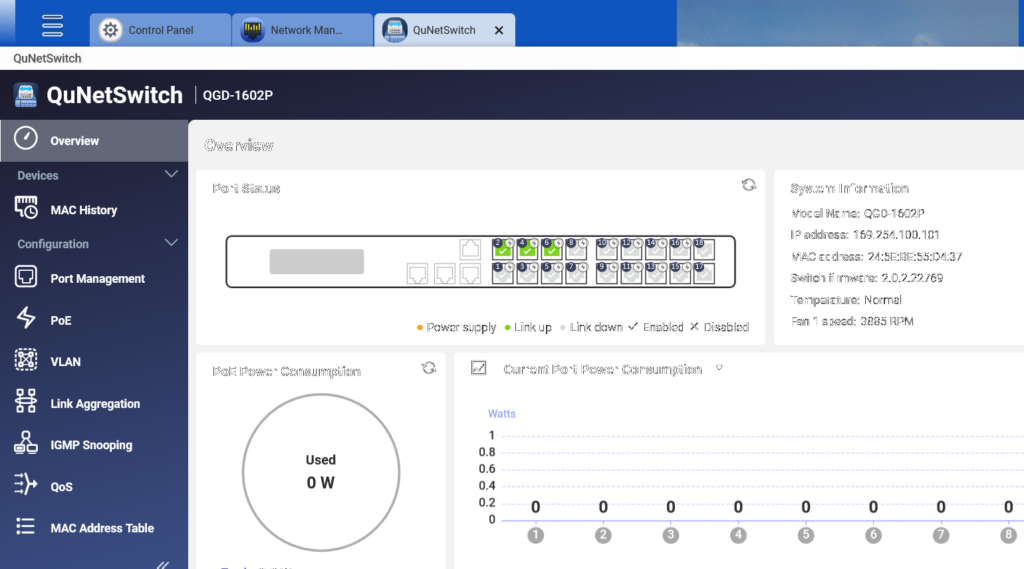
In the QuNetSwitch system interface, you can see the status indicators for different connected ports. On the left, network administrators can access familiar network switch configuration features, such as port management, PoE (Power over Ethernet), VLAN and other common standard setting functions.
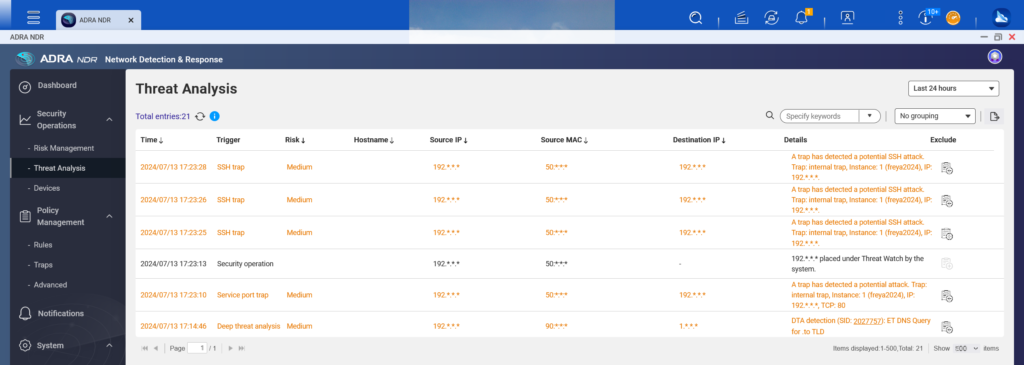
The most critical core feature of this product is the ADRA NDR networking endpoint protection. When accessing this page, you can navigate to the Threat Analysis tab, which records and provides explanations of malware activities, hacker login attempts, and other security incidents occurring in the OT network environment. If normal behaviors that are misidentified by the system are listed, they can be excluded. Carefully analysis is recommended.
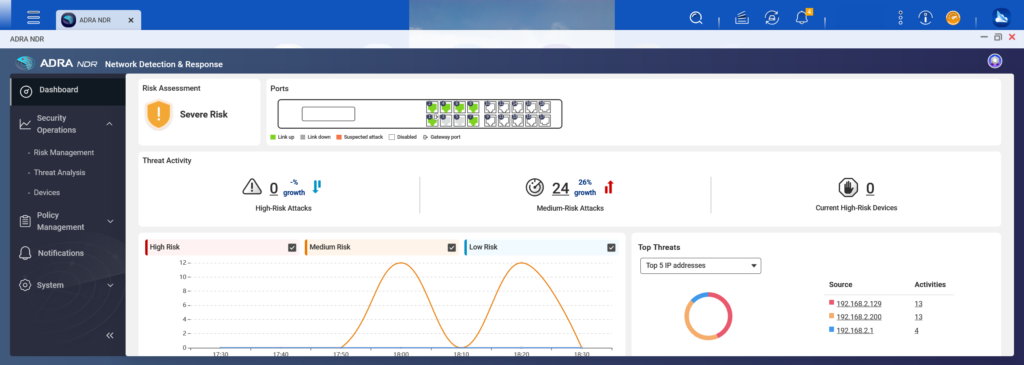
In security threat, visualized charts provide a display of primary threat source device IPs with trend analysis of various risks within OT network.
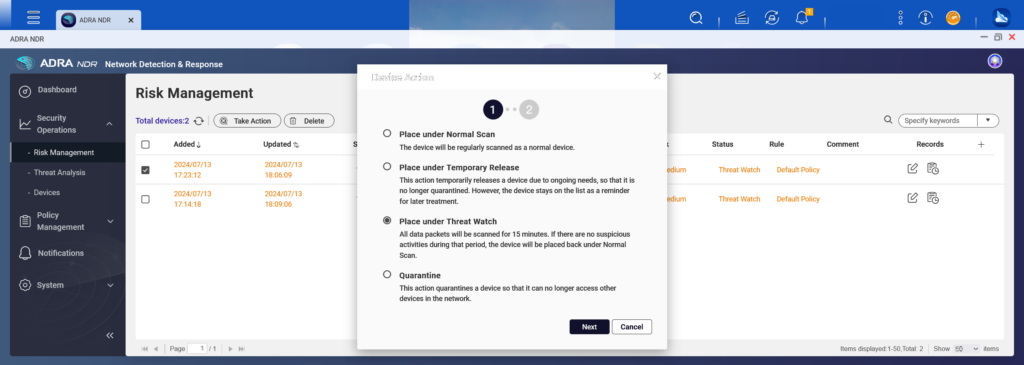
For risk management in OT networks, administrators can choose to either continue monitoring problematic devices or isolate them to prevent lateral connection and mitigate potential cybersecurity threats within the OT environment.
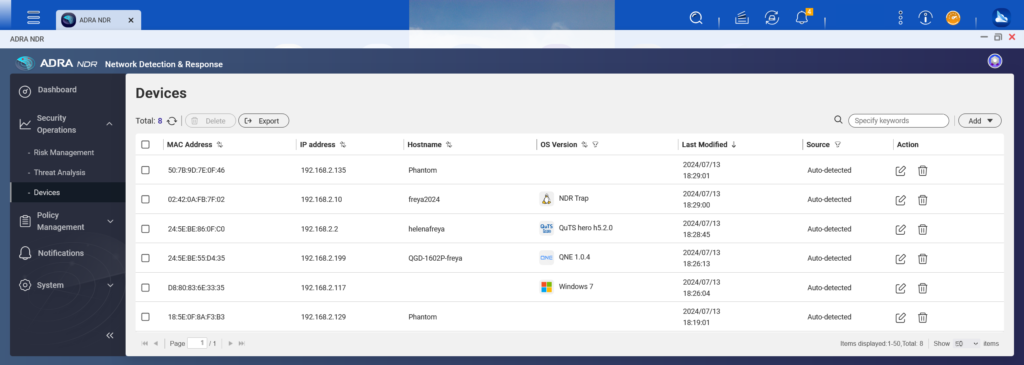
In ADRA NDR, a device list is displayed, allowing administrators to configure different actions for each device.
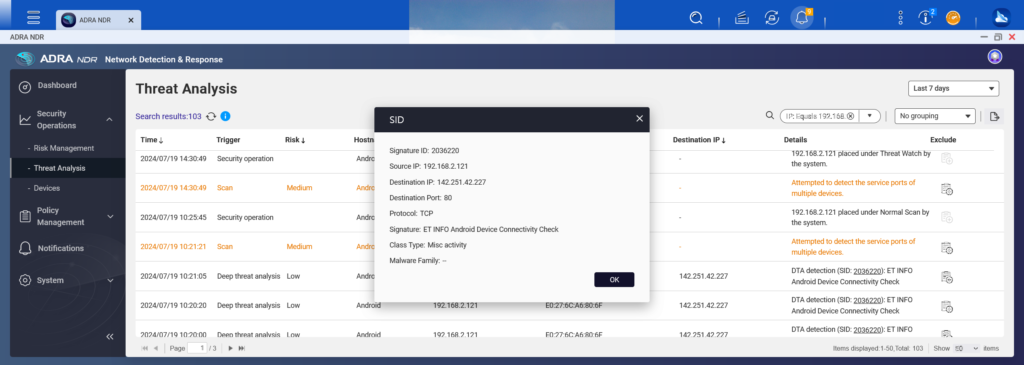
In the security threat analysis, you can access the threat data for this OT device.
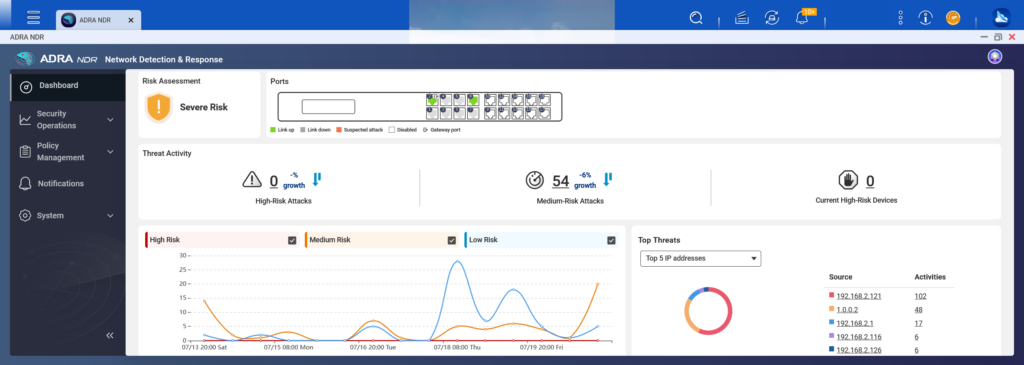
Visualized data can be tracked over the long term.
Key protection mechanisms provided for the OT area
1. Prevention of malware tampering and lateral spread
Since OT environments require high system stability, attacks such as ransomware, trojans, or worms can not only cripple production lines but also lead to significant safety risks and financial losses.
- Malware interception: A switch with built-in malware detection capabilities can intercept malicious files before they are transmitted to endpoint devices, preventing them from spreading across the entire factory network.
- Rapid incident reporting: When suspicious files or connections are detected, the system can immediately notify administrators, improving response handling time to threats.
2. Preventing unauthorized or malicious logins
If the devices within the OT system are compromised by a hacker login, the consequences could be catastrophic.
- Login Behavior Monitoring: By leveraging deep traffic and packet inspection, the switch can effectively identify abnormal login activities, such as unusual IP addresses, abnormal large-scale connection ports scanning, or excessive failed login attempts.
3. Enhancing overall security visibility and compliance
Implementing switches with built-in malware detection and behavior monitoring not only strengthens security protection but also helps manufacturers better meet various industrial security compliance requirements such as IEC 62443.
- Logging and auditing capabilities: The switch can provide comprehensive traffic logs and alert event reports, enabling administrators and auditors to track critical network activities. This enhances compliance with ISO 27001 implementation, internal audits, third-party external audits, or supply chain security audits.
4. Practical deployment recommendations
Identify key assets and high-risk areas
We usually begin by identifying critical equipment within the OT area, such as production line control devices and critical servers, along with nodes that are vulnerable to external connection threats. The next step is to prioritize the deployment or replacement of switches in high-risk areas. For example, replacing traditional switches with QGD-1602P is a highly practical approach. This upgrade enhances OT equipment protection without disrupting existing operations while simultaneously monitoring traffic and behavior, and maintaining records. This benefits future cybersecurity compliance and reduces the burden on network administrators.
Step-by-step deployment and verification
Start with a small-scale deployment in production or testing environments to observe its impact on traffic, performance, and stability. Verify that the monitoring, detection, and alert functions work correctly before gradually expand to the entire OT area.
Good log management and alert response process
Even with advanced malware detection and behavior monitoring capabilities, without a well-defined alert response process and proper log management and analysis tools, the system cannot operate at its full potential.
Collaborating with IT department
Although the requirements for OT and IT are not entirely the same, as OT typically prioritizes stability, avoiding frequent system updates or complex environment implementations that could impact the OT work area, in the vast majority of cases, OT systems cannot afford any downtime. IT, on the other hand, requires more timely updates, where fewer disconnections or reboots on the user end are more acceptable. However, this is not the case for OT.
In industrial computer OT environments, traditional switches primarily serve as a data transmission devices. However, with increasing complexity of security threats today, implementing switches with malware detection and device behavior monitoring capabilities at both the equipment and network layers can significantly strengthen protection capabilities against ransomware, trojan attacks, and unauthorized access.
These types of switches can start from the most basic packet inspection and behavior comparison, combined with real-time alerts and visualized information, offering superior security protection for OT environments compared to previous solutions. This is the key advantage of QNAP’s QGD series.