
In the military domain, “Defense in Depth (DiD)” is also known as “resilient defense” or “layered defense”. It uses comprehensive and multi-layered defense strategy or pre-emptive attacks to not directly prevent enemy’s advance but delay its progress. This strategy works by sacrificing some areas to buy time and force the enemy to spend more resources, making its attack lose its advantage, forcing it to retreat to the original starting attacking position, and even providing our side with opportunities to counterattack and reverse the situation.
Although large-scale warfare seems distant now to most people in today’s world, the principles of Defense in Depth are widely applied in many non-military domains, especially in security-related areas, including nuclear power plants and information security. It means implementing multiple safeguards to prevent accidents from happening and taking various measures to reduce losses after accidents have happened.
As enterprises and organizations expand the scale of their IT infrastructure, Defense in Depth strategies become even more important. As a leading brand in the field of network storage technology, QNAP has undergone many years of development and provides comprehensive security controls. From “management security control” to “physical security control” and “technical security control,” QNAP offers a complete solution that includes connection protection, threat trap, permission protection, transmission protection, security assessment, and disaster recovery.
|
| Built-in system | Install software package |
|
Connection protection |
| |
|
Threat Trap |
| |
|
Permission protection |
| |
|
Transmission protection |
| |
|
Security assessment |
|
|
|
Disaster recovery |
|
|
[Layer 1] Connection protection: QVPN, QuWAN, QuFirewall

When users connect remotely to their QNAP NAS, the first step in safe and efficient information protection is to secure connection and file transmission over the network.
QVPN Service: Safe and secure file transfer
VPN ensures the security of accessing network resources and services in public networks and prevents network traffic from being intercepted. QVPN service integrates both VPN server and VPN client functionalities to enable connections to remote servers or facilitate access to content or services via vendors’ VPN client. QVPN service supports the open-source OpenVPN service and integrates with popular OpenVPN services on the market, such as ExpressVPN™, NordVPN®, Surfshark®, Astrill®, etc., so as to provide more diverse VPN connection options to ensure a secure virtual private network.
By setting up QNAP devices through QVPN Service, you can connect to remote VPN servers, making access remote resources more secure, and eliminating geographical restrictions. The connection can also be further set up as the default gateway for QNAP devices, redirecting all outgoing network traffic to the VPN. QVPN device client supports QBelt and other protocols and can connect to QNAP devices through VPN. Connection logs are kept for viewing historical usage data, and a built-in speed test feature can help evaluate VPN connection speeds.
QuWAN: Building a new agile IT architecture for small and medium-sized enterprises
Software-Defined Network (SDN) has changed the way of data flow control in traditional networks. It separates the “control plane” of network devices and consolidates it into an external server as a centralized controller to manage all devices involved in packet forwarding paths. This allows network system administrators to have a global view and makes the entire network act like a huge programmable software that can be dynamically adjusted at any time according to different business needs. One of the most prominent SDN use cases is the B4 wide area network (WAN) used by Google to connect data centers around the world, which triples the bandwidth utilization to nearly 100%, making the network more stable and easier to manage.
In addition to improving bandwidth and facilitating management, information security based on policy deployment has always been an area that is very suitable for SDN application. With traditional enterprise network architecture, connecting multiple locations typically requires connection to headquarters, which often encounters bottleneck issue due to insufficient bandwidth. However, enterprise-level VPN equipment on the market is expensive and time-consuming to deploy, and unaffordable for ordinary small and medium-sized enterprises.
QNAP SD-WAN (QuWAN) uses advanced virtualization technology to automatically configure all externally connected WAN services and quickly establish a mesh virtual private network (Auto Mesh VPN). This enables multiple branch units to flexibly form networks at any branch, with a low-cost, highly flexible network deployment architecture. It optimizes network bandwidth and makes it easier for enterprise employees to access internal systems from the company’s intranet. At the same time, network segmentation helps limit internal data and information exposure to users outside the company.
Software-defined networking also facilitates security analysis and load balancing. QuWAN utilizes Deep Packet Inspection (DPI) technology to detect terminal services at the application layer and to effectively identify the websites, devices, and potential viruses which packets originate. It can also customize critical business applications, allocate higher bandwidth priority to them, and provide a smooth network experience. Additionally, with the L7 firewall feature, it can automatically detect malicious packets, blacklist specific applications and block them to ensure enterprise network security.
myQNAPcloud Link: Simple and secure remote connection service
myQNAPcloud Link is a remote connection service provided by QNAP, which allows you to connect to QNAP devices through the myQNAPcloud website (www.myqnapcloud.com) over the Internet. No complex router settings are required. You only need to install the myQNAPcloud Link app, register a QNAP ID on your device, and then log in to the myQNAPcloud website using your QNAP ID to connect to your QNAP device.
QuFirewall: QNAP device-specific firewall
In line with the popular Zero Trust Networks concept, you can install and enable QuFirewall on QNAP devices to establish a host-based “micro-perimeter” firewall to protect important data and services. You can also integrate other security features on QNAP devices, such as user authentication and permission settings, to make the devices more robust and highly resistant to hackers and malware and other threats.
[Layer 2] Threat Trap: ADRA NDR

In the field of information security, behavioral analysis is a key technology. It can help us trigger the security system in time and prevent the execution of attacks when abnormal traffic and attack behaviors are detected.
QNAP has introduced subscription-based NDR (Network Detection & Response) in the QGD series access switches, which selectively and quickly screens some network traffic through Threat Watch, which is efficient and does not reduce speed. It also uses Threat Trap to simulate the trapping mechanism of common network services to detect intranet penetration activities of targeted ransomware and other malicious software at an early stage. Combined with countermeasures such as in-depth threat analysis, threat correlation analysis, and precisely targeted automatic blocking of infected devices, the spread of malicious software such as targeted ransomware on the intranet is blocked to ensure the information security of enterprises and organizations and protect them from harm.
[Layer 3] Permission protection: delegated administration, AD/LDAP, two-factor authentication
In the field of information security, in addition to technical security controls to prevent data leaks, network attacks and other threats, administrative security controls are also crucial. Administrative security controls refer to the principles set by system administrators and security teams to control access to internal systems, company resources, and other sensitive data and applications to avoid exposing systems, devices, and applications to unnecessary human-related risks. This is also an integral part of information security.
Delegated administration: division of roles
The principle of least privilege access refers to granting users only the system and resource access permissions necessary for their roles. This approach helps minimize the risk to other parts of the network from unauthorized users performing attacks or accessing sensitive data.
As an organization grows, the number of employees and devices also increases. Having a limited number of IT administrators to manage the continuously growing number of accounts and devices can result in a heavy workload that can impact day-to-day productivity and lead to frequent errors. When employees only require access to certain NAS functionalities or tasks, granting permissions beyond what is necessary may lead to security risks for the NAS and its data. When system administrators are not in the office or unable to address tasks immediately, if there’s no other personnel with appropriate permissions to provide assistance, especially during emergencies, it might lead to potential disaster.
Therefore, carefully delegating “appropriate permissions” can improve productivity, ensure data security, and facilitate team collaboration. Granting limited permissions to perform application tasks and data access can not only reduce IT administrators’ workload, but also enable department managers to have greater control over data. This results in higher productivity and data security for the organization due to decentralization and division of responsibilities.
AD/LDAP: Centralized control of permissions
For enterprises, setting up an LDAP server implies additional hardware expenses. Fortunately, the QPKG page of the QNAP official website provides an OpenLDAP package. After installation, the QNAP NAS can be converted into an LDAP server. Following the same logic, other servers that support the LDAP protocol can join the QNAP NAS, which has been upgraded to an LDAP server and allows them to provide unified authentication accounts.
Another option is to rent JumpCloud’s cloud LDAP service, so that the QNAP NAS can become a hybrid cloud data operation center and provide cloud directory service (Directory as a Service), and centralize services originally provided by the LDAP server in the cloud. From the JumpCloud website, a centralized global colleague login mechanism can be provided for IT colleagues around the world to individually set up consistent LDAP servers without the need of training and coordination.
This not only allows users to use a set of JumpCloud accounts and passwords to log in to various office devices in the same domain around the world, such as printers and public folders on all NAS, or over 100 cloud services like Office 365, AWS, or G Suite, but also use it for authorizing office WiFi access or logging into various local cloud systems within the company.
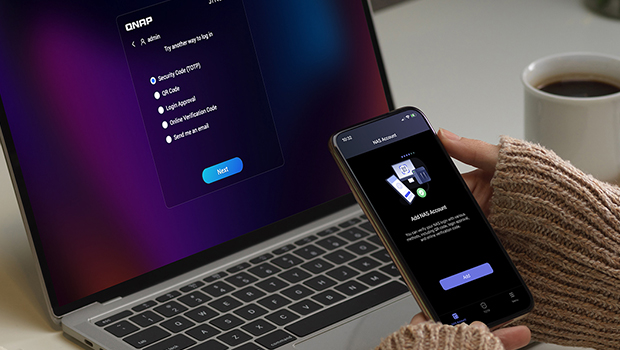
Two-factor authentication: Identity verification
Research has shown that multi-factor authentication provides better resistance against malicious attacks. Today, simply relying on a strong password policy or using complex passwords is no longer enough to fully protect your NAS from unauthorized access.
You can significantly enhance data security and effectively prevent malicious network attacks by installing the QNAP Authenticator app on your mobile device and setting up two-factor authentication for your NAS, which supports time-based one-time password (TOTP), one-time password (OTP), QR code scanning, or one-click login approval.
[Layer 4] Transmission protection: SMB encryption, latest self-encrypting drive
“Physical security controls” are important measures to ensure that IT systems are protected from threats such as tampering, theft or unauthorized access, and data encryption is one way to protect sensitive information within this context. Encryption is the process of converting readable text into unintelligible ciphertext to prevent access by unauthorized or malicious parties, which is critical to network security. QNAP offers a range of solutions that cover everything from data transfer to storage on the hard drive.
SMB (Server Message Block) is a protocol for network file sharing that allows applications to read and write files on a computer or request services from server programs on the network. The SMB protocol uses TCP/IP or other network protocols for file sharing and accessing folders or other data on a remote server, including applications reading, creating, and updating files on the remote server. SMB 3.0 provides end-to-end encryption to enhance security and mitigate the risk of data being intercepted in untrusted network connections. The main benefits are that it eliminates additional costs for deployment, for specific hardware or WAN accelerators while further enhancing Internet Protocol security (IPSec).
QTS 5.0 supports AES-NI hardware acceleration, which boosts the efficiency of packet signing, transmission encryption and decryption in the SMB 3 transmission protocol, making it up to 5 times faster compared to when AES-NI hardware acceleration is not present. While protecting important data, system performance remains efficient. QuTS hero h5.1.0 supports the latest AES-128-GMAC signature acceleration (only applicable to Windows 11® and Windows Server 2022® clients) to significantly enhance the efficiency of data packet signing in the SMB 3.1.1 transmission protocol. This results in better CPU utilization and provides the optimal combination of performance and protection.
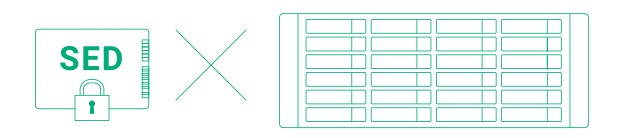
Self-Encrypting Drive (SED) encrypts the entire hard drive through its built-in encryption processor, providing the final layer of protection for information security. In addition to supporting TCG-OPAL and TCG-Enterprise protocols, QTS 5.2 also adds support for mechanical hard drives and solid-state drives that comply with the TCG-Ruby SED standard, and provides specifications for NVMe and other new disk technologies. It is more in line with current enterprise and data center needs and makes it easier to comply with regulatory requirements such as GDPR, HIPPA, and HITECH.
[Level 5] Security Assessment: Security Center, Notification Center
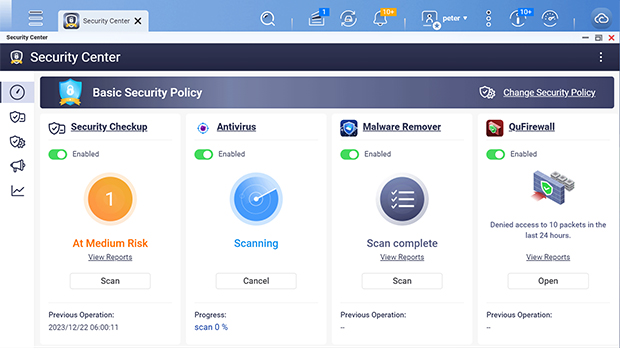
Prevention is better than cure. The newly added Security Center in QTS 5.2 can serves as the security hub for QNAP NAS. It integrates file activity monitoring, proactive protection measures, scanning of NAS security status, immediate alert notifications, and antivirus software integration. It actively analyzes and monitors NAS system status, file activities, and potential network security threats, conducts security risk assessments, and assists users in taking immediate protective measures to prevent data loss and security vulnerabilities.
In addition, the Security Center has added a new feature called “Anomaly File Activity Monitoring” to monitor file activities at any time and closely detect NAS file activity status and abnormality risks. Users can utilize the visual monitoring interface to quickly grasp the average file modification volume within a specific time period. At the same time, users can customize protection measures to respond to alert events when the number of file changes exceeds the threshold, such as immediate protection (read-only mode), immediate backup (taking snapshots), and immediate blocking (pausing snapshot schedule). This minimizes the risks and damages of data loss caused by threats such as crypto-ransomware, malware attacks, or human errors, and makes managing NAS security more efficient and comprehensive.
Users needing more extensive system real-time information can go to the existing QTS Notification Center which integrates all QTS system events, alerts and notifications into a single application. Users can centrally manage all notifications without the need to configure them individually in each application. This allows users to easily monitor the status of the NAS at any time and quickly configure notification settings and view system logs through a single window.
[Layer 6] Disaster recovery: SnapShot, SnapSync, Backup, Malware Remover, ADRA NDR
Data storage, sharing, backup and restoration have always been the strengths of QNAP NAS. It comes with the feature of automatically updating the latest malware definition files, and the ability to directly isolate devices affected by malware on the access switch to greatly enhance defense capabilities against malware. This helps contain attacks within a minimal scope and enables swift disaster recovery.
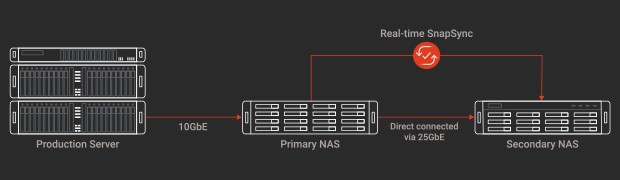
The snapshot function is just like taking a photo. It can record the system status and data at any point in time as a backup for future restoration. Snapshots use less storage space than traditional backups. When the NAS data is damaged or the computer is threatened by encrypted ransomware, snapshots can be used to quickly restore it to ensure that important data is not lost. SnapSync uses block-level remote backup to instantly back up data from one QuTS hero NAS to another, reducing backup time and risk of data loss.

Hybrid Backup Sync is a license-free multi-service file backup, recovery and synchronization solution that ensures uninterrupted enterprise operations. Whether it’s local, remote, or cloud backup, Hybrid Backup Sync can perform bidirectional backup, recovery, and data synchronization to local storage, cloud services, or remote servers and provide comprehensive data protection.
Malware Remover can regularly scan the NAS to check and download the latest malware definition files. When attacked, it can remove the malicious code and restore the system settings and files affected by the malicious program, thus improving the security protection level of NAS. ADRA NDR ensures that unaffected devices remain unharmed without the need to disconnect all network connections. The QNAP NAS can restore data to the previous intact point in time, significantly reducing the time required for cybersecurity investigations. This allows for the swift restoration of employee work computers and essential services for company operations.
The most important line of defense: cybersecurity awareness
Ultimately, no matter how advanced cybersecurity technologies are, they are merely “tools”. The effectiveness depends on whether users have sufficient cybersecurity awareness to utilize them effectively. Cybersecurity awareness refers to the awareness and understanding of information security risks as well as the implementation of appropriate measures to protect information from threats and attacks. With the rapid development of information technology, cybersecurity risks are also constantly increasing. Under such circumstances, raising cybersecurity awareness has become the most important line of defense for data protection.